Going to DEF CON was a dream I never thought would come to fruition. I remember 2009 being in 8th grade. Reading a physical copy of the magazine Wired. Sitting in the back of parent's minivan on the way to visit family in Milwaukee, WI, and seeing pictures and reading about the largest hacking conference in the world. There were hackers getting arrested, voting machine hacking, lock picking, and hacker jeopardy. That dream came true in 2016 at DEF CON 24.
At DEF CON 31 I returned to speak at the Hardware Hacking Village. My first time speaking at DEF CON was full of anxiety, as the Sunday before flying out I was testing the hardware and I found out I ordered the ESP-01 and not the ESP-01S. I was up until 1 AM trying to get it to work anyway, but ended up putting in a last minute Amazon order (at twice the price of AliExpress) to get the ESP-01S's I needed. Thankfully the Amazon delivery arrived that Tuesday and we flew out Wednesday evening.
My talk (Introduction To Esp8266/Esp32 Microcontrollers And Building A Wi-Fi Deauthentication Detector):
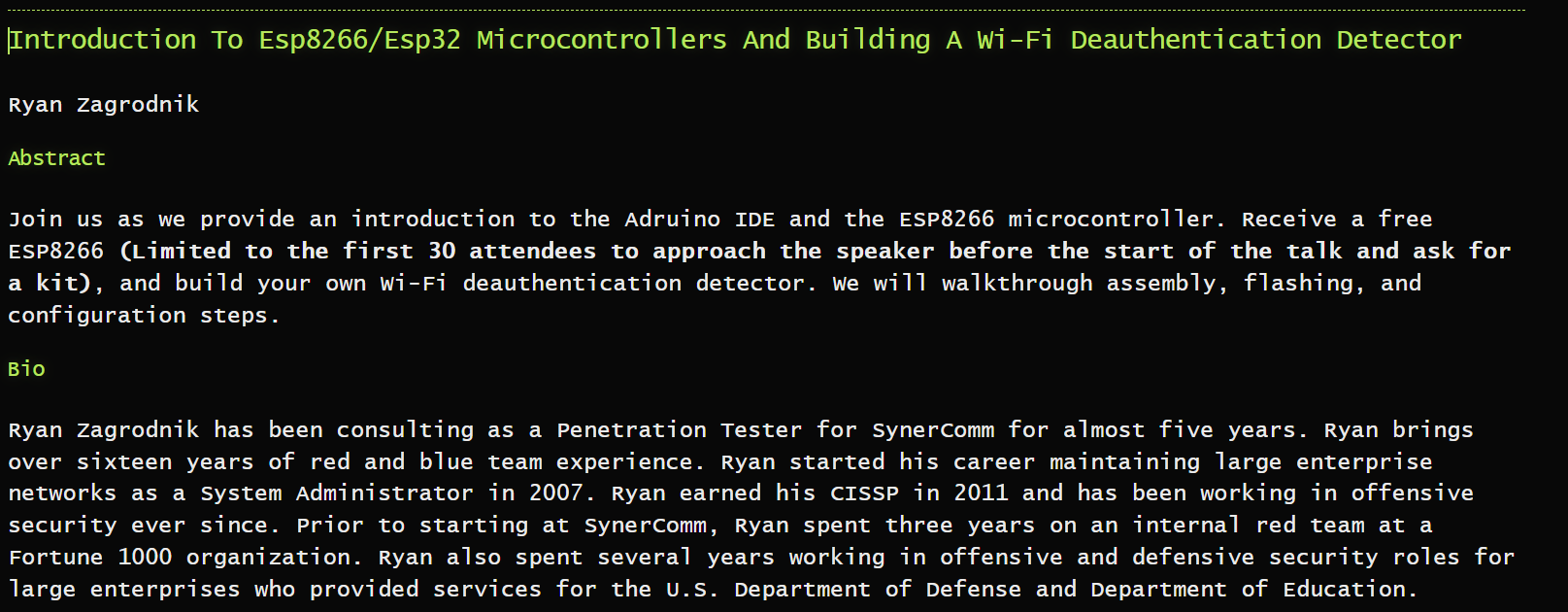
TL;DR of my talk:
Slides are available here: https://twitter.com/TheL0singEdge/status/1690142545605791752
Lesson's Learned:
DEF CON 31 Tool Highlights:





References:
https://media.defcon.org
https://www.flickr.com/photos/r6_cannibal/albums/72177720310525638/
https://twitter.com/search?q=%23defcon

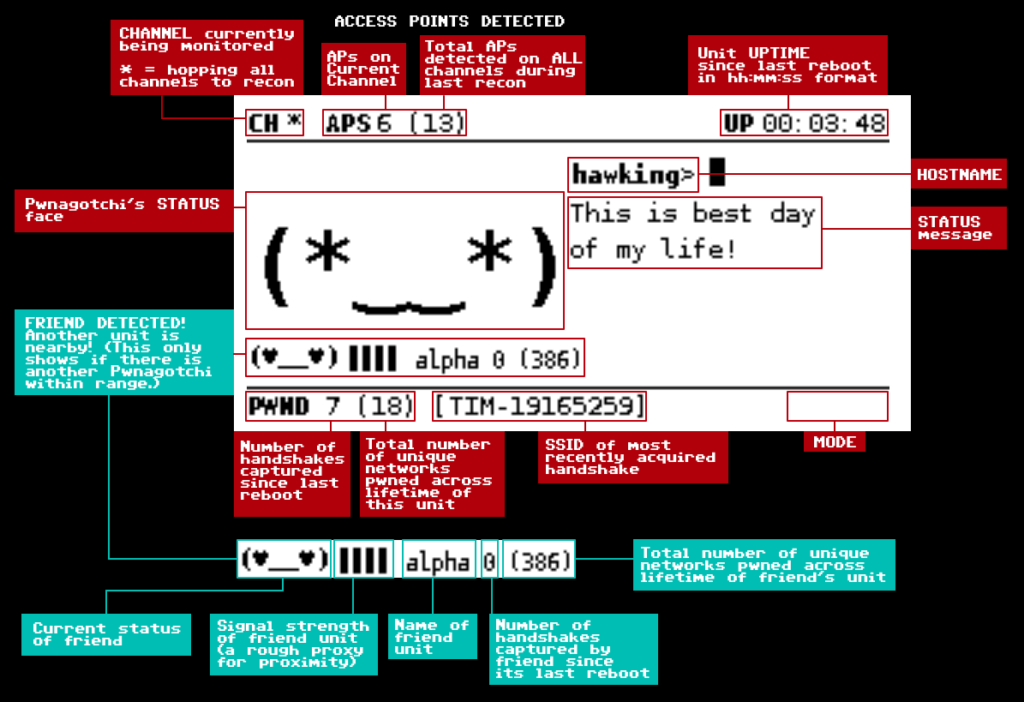
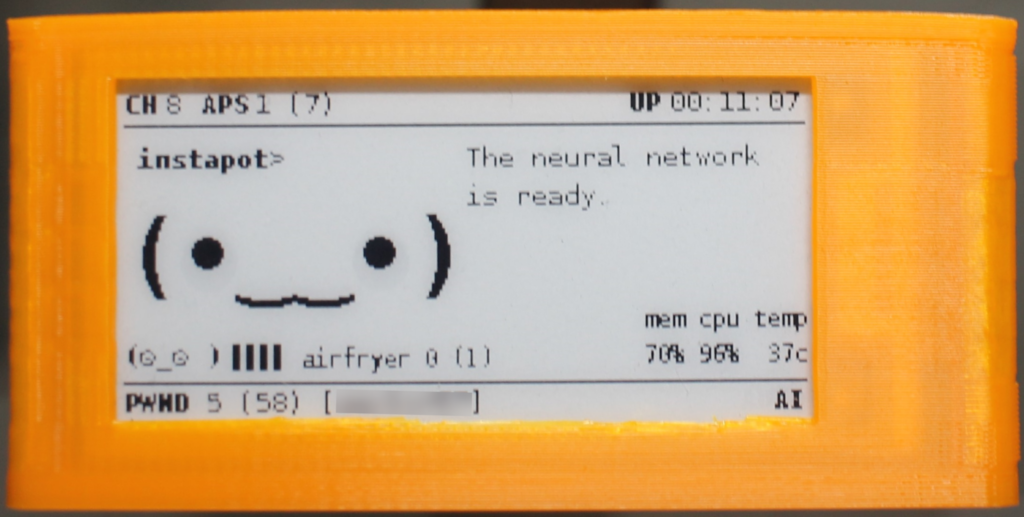
Pwnagotchi is an A2C-based “AI” powered by bettercap and running on a Raspberry Pi Zero W that learns from its surrounding WiFi environment in order to maximize the crackable WPA key material it captures (either through passive sniffing or by performing deauthentication and association attacks). This material is collected on disk as PCAP files containing any form of handshake supported by hashcat, including full and half WPA handshakes as well as PMKIDs.
https://pwnagotchi.ai/intro/
In case you're curious about the name: Pwnagotchi (ポーナゴッチ) is a portmanteau of pwn and -gotchi. It is a nostalgic reference made in homage to a very popular children's toy from the 1990s called the Tamagotchi. The Tamagotchi (たまごっち, derived from tamago (たまご) "egg" + uotchi (ウオッチ) "watch") is a cultural touchstone for many Millennial hackers as a formative electronic toy from our collective childhoods.
Each state and country has their own laws pertaining to the unauthorized access and collection of data.



From https://pwnagotchi.ai/installation/#flashing-an-image:
The easiest way to create a new Pwnagotchi is downloading the latest stable image from our release page and writing it to your SD card.
Once you have downloaded the latest Pwnagotchi image, you will need to use an image writing tool to install that image on your SD card. We recommend using balenaEtcher, a graphical SD card writing tool that works on Mac OS, Linux, and Windows; it is the easiest option for most users. (balenaEtcher also supports writing images directly from the ZIP file, without any unzipping required!)
To write your Pwnagotchi image with balenaEtcher:
- Download the latest Pwnagotchi .img file.
- Verify the SHA-256 checksum of the .img
- Download balenaEtcher and install it.
- Connect an SD card reader with the SD card inside.
- Open balenaEtcher and select from your hard drive the Raspberry Pi
.imgor.zipfile you wish to write to the SD card.- Select the SD card you wish to write your image to.
- Review your selections, then click
Flash!to begin writing data to the SD card.As an alternative you can use dd on GNU/Linux or macOS:
Change the path to your image file,
/dev/sdcardis the path to you SD card device.dd if=path/to/pwnagotchi-raspbian-lite-XXX.img of=/dev/sdcard bs=1MWait before removing the SD card as you will need to create one last file on it with the initial configuration.
https://pwnagotchi.ai/installation
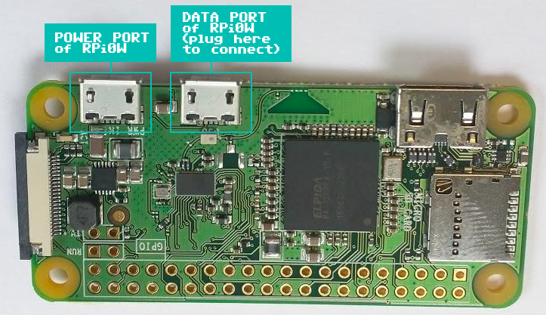
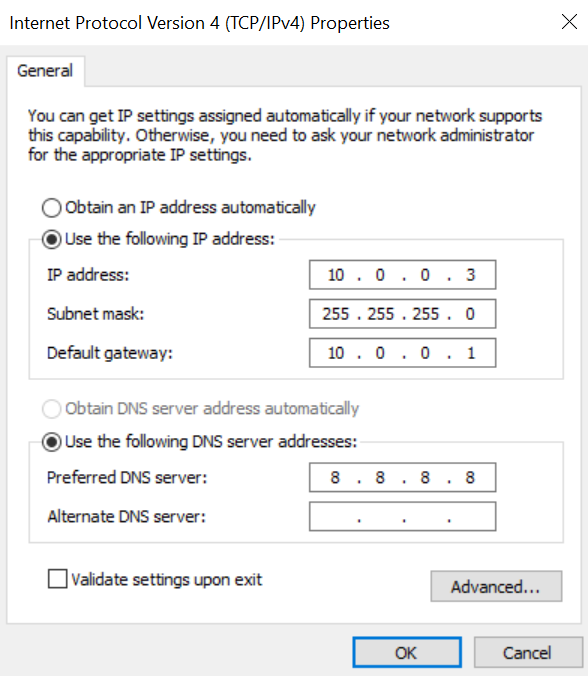
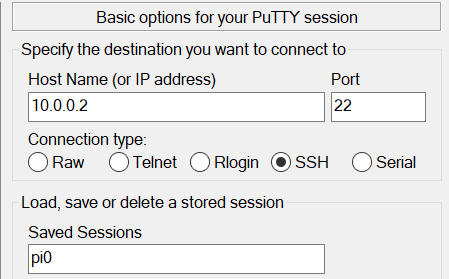
Edit the config located in /etc/pwnagotchi/config.yml, restart, and you should be good-to-go.
# Add your configuration overrides on this file any configuration changes done to default.yml will be lost!
# Example:
#
# ui:
# display:
# type: 'inkyphat'
# color: 'black'
#
main:
name: '<NAMEOFPWNAGOTCHI>'
whitelist:
- '<YOURNETWORK>'
plugins:
grid:
enabled: false
report: false
exclude:
- '<YOURNETWORK>'
ui:
display:
enabled: true
type: 'waveshare_2'
color: 'black'
web:
username: pi
password: <YOURPASSWORD>