One of the things I have noticed while working at SynerComm over the years is that while most companies have employees on staff who possess the necessary technical knowledge to complete their...

Insights From Cybersecurity Experts

One of the things I have noticed while working at SynerComm over the years is that while most companies have employees on staff who possess the necessary technical knowledge to complete their...

Why Trust is Essential Our valuable experience is both deep and broad. We have extensive experience with IT infrastructure, security, operations, management, and logistics, allowing us to serve our...
SynerComm partnered with ChannelBytes to present 60 minute session where we discuss what it means to do quality, modern penetration testing in 2020. Penetration testing is a core part of the...

Participating in Black Hat USA 2020, we sat down with Dark Reading where our own Brian Judd, VP Information Assurance discusses how we are innovating and evolving penetration testing. See more at...

Although contingency planning has a healthy focus on technology, it still requires people to interface with that technology, configure and program the technology so that it will perform some...
The COVID-19 event, obviously, has had a wide-reaching negative impact for the entire country. Despite this, even in the face of the trauma linked to the loss of loved ones, we will eventually...

“So, let’s say we fix all of the vulnerabilities that the pentest discovers… How do we know tomorrow that we’re not vulnerable to something new?” ~Customer Bridging the Gap Between...

Trying to find qualified IT infrastructure and security people? We at SynerComm help companies successfully overcome that challenge every day, and so I suppose I suffer from the old adage: “to a...
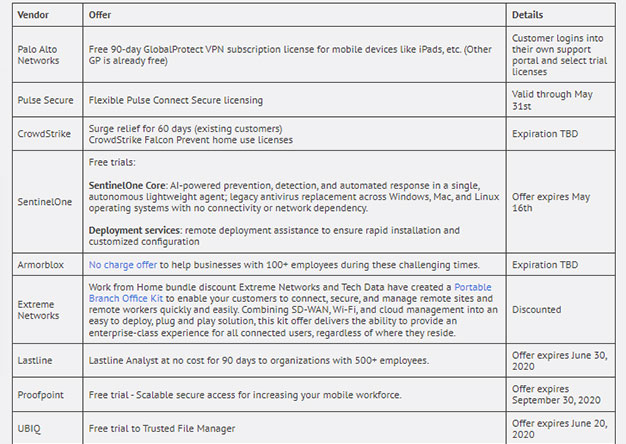
Most enterprises are getting slammed with employees working from home. Most of us designed our remote user VPN’s for the occasional "snow day" ...right. Now we have an entire workforce, working from...
Practicing good remote access hygiene in times of uncertainty As the business world reacts to the current health crisis, companies are offering remote access to any role that can work from home....