Resources
How Critical is Data Visibility for Network Security
Having access to data on a network, whether it’s moving or static, is the key to operational efficiency and network security. This may seem...
Common Pitfalls to Avoid in International IT Systems Deployment
When US based companies are expanding and setting up offices in foreign countries, or they’re already established but need to do a systems...
Password Hash Cracking with the NVIDIA RTX 4090
In February 2017, I co-authored a blog detailing our build of an 8-GPU password cracker. Over the past 8 years, it’s had millions of views and...
SynerComm Selected as SC Media Trust Award Finalist
SynerComm's Continuous Attack Surface Management (CASM Engine®) and Continuous Penetration Testing was named a top-five finalist in the Best...
shellntel.com has moved
I can remember it like it was yesterday... Casey, Hans, Jason, Scott, Sam, Bill and I were slowly destroying my hotel suite at Circle City Con...
Build a Cheap Gigabit Network Tap
Whether doing security research or troubleshooting networks, network sniffers and packet analysis can be invaluable tools. If you're a network...
Who Does the GLBA Safeguard Rule Apply To?
Why the GLBA Safeguard Rule change might apply to your business Back in 1999, the Gramm-Leach-Bliley Act was passed in the United States. Its...
IT Trendsetters with Check Point
SynerComm and ChannelBytes hosted an engaging virtual discussion with Check Point, touching on topics ranging from “Innovative ways Check Point...
IT Trendsetters episode with Expel
SynerComm and ChannelBytes hosted an engaging virtual discussion with Expel, touching on topics ranging from “Advancements from SIM...
Surviving the Ransomware Siege
See the original publication found in On Balance Magazine. At some point in 2015, cybercriminals had an aha moment. Instead of going through all...
SynerComm Inc. Recognized as 2020 North America “Overall” Partner of the Year by Juniper Networks
SynerComm Inc. is proud to announce it has been named a 2020 “Overall” Partner of the Year by Juniper Networks. Selected out of 1,000 plus...
I have M365 for our Enterprise email… OMG how to deal with the outages?
Another M365 email outage... seriously just Google it... there are even multiple websites that monitor and tell you there is an outage but there...
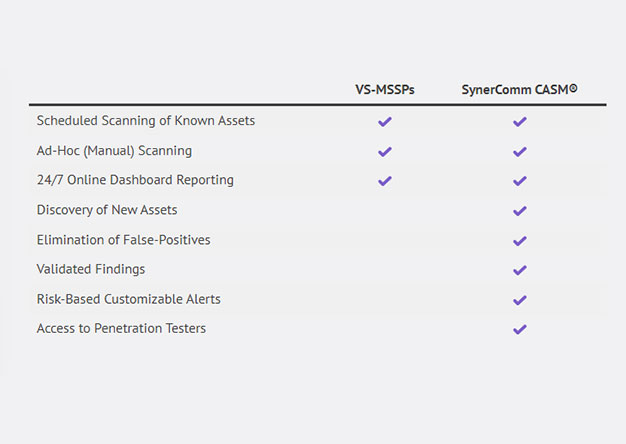
Time to Upgrade from Outdated Managed Vulnerability Scanning to Continuous Attack Surface Management
Warning: This blog contains purposeful marketing and gratuitous plugs for SynerComm’s CASM™ Subscription services. Seriously though, the...
In Scope or Out of Scope?
#_SHELLNTEL In penetration testing, it’s important to have an accurate scope and even more important to stick to it. This can be simple when the...
Empowering Your Project Manager: The Benefits of an IT Focused Approach to Logistics
One of the things I have noticed while working at SynerComm over the years is that while most companies have employees on staff who possess the...