Resources
Evading Defender by Embedding Lua into Rust
I recently started learning about the world of game modding. I have always played games on a console, so modding...
The Cybersecurity Framework Gets a Facelift
NIST CSF 2.0 brings new content to broaden its audience and new tools to help ease implementation. By Jeffrey T....
AI and Machine Learning in Threat Detection: Navigating Advancements and Challenges (Part 2)
In part one of this series, we discussed the evolving landscape of cybersecurity and the roles artificial...
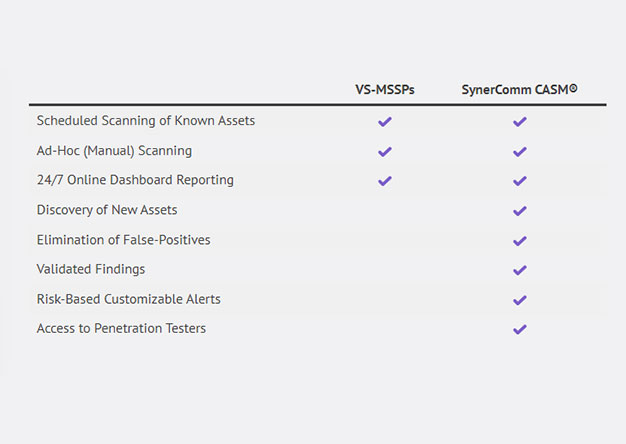
Beyond Vulnerability Scanning: Strengthening Perimeter Cybersecurity
Over the past 20-years, I’ve used every major vulnerability scanner. There are several great scanners on the...
AI and Machine Learning in Threat Detection: Navigating Advancements and Challenges (Part 1)
With the help of artificial intelligence (AI) and machine learning (ML), cybercriminals are creating novel,...
Attacks on Active Directory Certificate Services (AD CS) Explained – CypherCon 2024 Follow-up
This is a follow-up blog post from our CypherCon 2024 presentation. The slides are located here:...
Exploring Initial Access Methods #01 – Shortcuts and Tunnels to the Kingdom
Understanding the various methods and Tactics, Techniques and Procedures (TTP's) by which attackers gain initial...
Continuous Pentesting and Its Many Names
Are you looking for a pentest? A continuous pentest? Or maybe attack surface management? We’ll never have a...
Strengthening Healthcare Defenses
In the dynamic realm of cybersecurity, the healthcare industry has become a prime target for malicious actors...
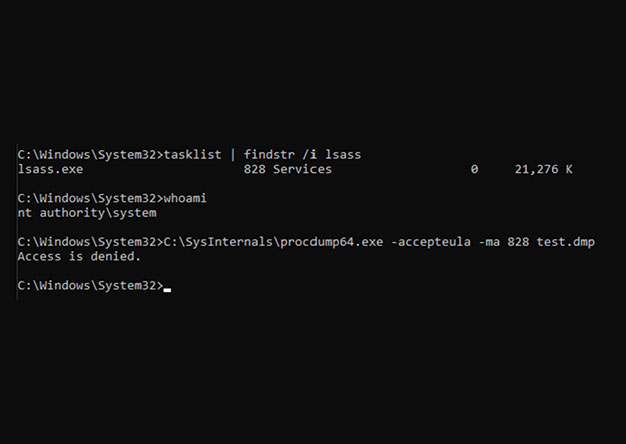
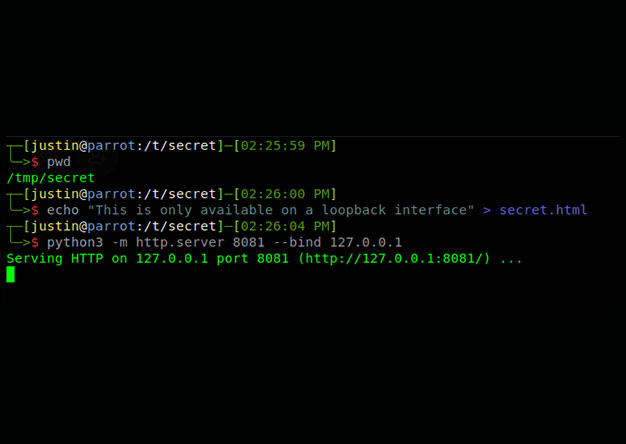
Spoofing Command Line Arguments to Dump LSASS in Rust
One of the popular methods for dumping LSASS is using the procdump.exe program from the Sysinternals Suite....
The Future of Business Applications and Data Center Access: Insights from SynerComm’s IT Summit
The recent 20th Anniversary of IT Summit was an eye-opener for tech enthusiasts, security professionals, and...
Navigating the Skies: TSA’s New Cybersecurity Requirements for Airlines
In today's increasingly digital world, the aviation industry is more reliant on technology than ever before. As...
Creating a Rootkit to Inject into a Protected Process and Dump LSASS
In my last blog post, I discussed one method of dumping LSASS where we created a DLL that we injected into Task...
DEF CON 31 and Building A Wi-Fi Deauthentication Detector
Going to DEF CON was a dream I never thought would come to fruition. I remember 2009 being in 8th grade. Reading a...
Rotating Your Pentesting Vendor Is A Mistake!
Having sold and performed assessments and pentests for nearly 20 years, I’ve had plenty of opportunities to hone my...
Fun with AD CS from Windows Command Line
I’m a fan of full featured and weaponized C2s as much as anyone else to save time if it makes my job easier....
Common Cybersecurity Pitfalls to Avoid in 2023
In today’s business world, most companies are fully reliant on technology to maintain their daily operations. Data...
Using API Hooking to Dump LSASS with Task Manager Undetected
There are many ways to create an LSASS dump file. One of the easiest ways is with Windows Task Manager. Simply...
Infographic: Password Best Practices
Are you concerned about keeping your online account, personal information, and business accounts secure? Check out...
Executing Shellcode with Rust, AES-256, and a Gnome Photo
Intro Disclaimer: this research is intended exclusively as an intellectual exercise and a means of making defenders...
Is Your Outdated Infrastructure Holding Your Business Back?
There are few things more frustrating in business than systems that don’t work as efficiently as they should. With...
Understanding Cloud Security Management Posture
Many companies host their systems and services in the cloud believing it’s more efficient to build and operate at...
Scheduled Tasks With Lucee: Abusing Built In Functionality For Command Execution
What is Lucee? Lucee is an open-source Cold Fusion Markup Language (CFML) application server and engine intended...
Cybersecurity- What Are The Top Attack Trends In 2023?
The most recent quarterly threat report issued by Expel at the end of 2022, revealed some interesting trends in...
Attacks on AD CS and the Impact on Business
Active Directory Certificate Services (AD CS) are a key element of encryption services on Windows domains. They...
Connections And Vulnerabilities -What Should Your Business Know?
It’s estimated that in 2022 there are more than 23 billion connected devices around the world. In the next two...
Why QR Codes Are No Different From Spam Email
The use of QR codes has grown exponentially in the last few years. So much so that the software for reading QR...
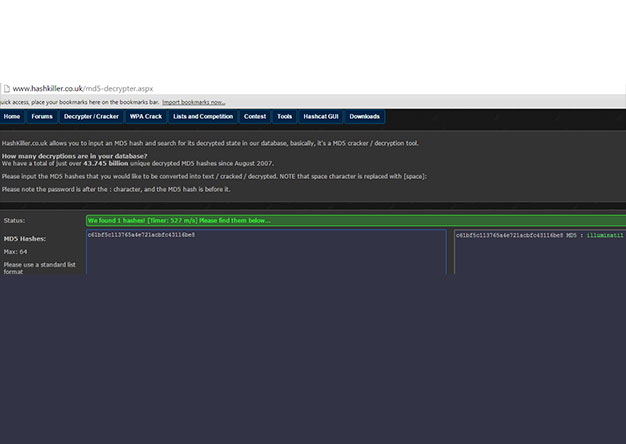
What Does Chat GPT Think About Password Hash Assessments?
SynerComm's marketing team likes to ask our pentesters for help with their messaging. Like all good hackers, we...
What Makes a Champion DNS Security Solution?
In boxing, the attributes that make up a champion are universally understood. A swift jab, a bone-crunching cross,...
Cloud Security – How to Find (and Fix) Hidden Vulnerabilities
Consolidating data centers, increased business agility and reduced IT system costs are a few of the benefits...
How Critical is Data Visibility for Network Security
Having access to data on a network, whether it’s moving or static, is the key to operational efficiency and network...
Common Pitfalls to Avoid in International IT Systems Deployment
When US based companies are expanding and setting up offices in foreign countries, or they’re already established...
Password Hash Cracking with the NVIDIA RTX 4090
In February 2017, I co-authored a blog detailing our build of an 8-GPU password cracker. Over the past 8 years,...
SynerComm Selected as SC Media Trust Award Finalist
SynerComm's Continuous Attack Surface Management (CASM Engine®) and Continuous Penetration Testing was named a...
shellntel.com has moved
I can remember it like it was yesterday... Casey, Hans, Jason, Scott, Sam, Bill and I were slowly destroying my...
Build a Cheap Gigabit Network Tap
Whether doing security research or troubleshooting networks, network sniffers and packet analysis can be invaluable...
Who Does the GLBA Safeguard Rule Apply To?
Why the GLBA Safeguard Rule change might apply to your business Back in 1999, the Gramm-Leach-Bliley Act was passed...
IT Trendsetters with Check Point
SynerComm and ChannelBytes hosted an engaging virtual discussion with Check Point, touching on topics ranging from...
IT Trendsetters episode with Expel
SynerComm and ChannelBytes hosted an engaging virtual discussion with Expel, touching on topics ranging from...
Surviving the Ransomware Siege
See the original publication found in On Balance Magazine. At some point in 2015, cybercriminals had an aha moment....
SynerComm Inc. Recognized as 2020 North America “Overall” Partner of the Year by Juniper Networks
SynerComm Inc. is proud to announce it has been named a 2020 “Overall” Partner of the Year by Juniper Networks....
I have M365 for our Enterprise email… OMG how to deal with the outages?
Another M365 email outage... seriously just Google it... there are even multiple websites that monitor and tell you...
Time to Upgrade from Outdated Managed Vulnerability Scanning to Continuous Attack Surface Management
Warning: This blog contains purposeful marketing and gratuitous plugs for SynerComm’s CASM™ Subscription services....
In Scope or Out of Scope?
#_SHELLNTEL In penetration testing, it’s important to have an accurate scope and even more important to stick to...
Empowering Your Project Manager: The Benefits of an IT Focused Approach to Logistics
One of the things I have noticed while working at SynerComm over the years is that while most companies have...
The Benefits of a Partnership Built on Trust
Why Trust is Essential Our valuable experience is both deep and broad. We have extensive experience with IT...
Penetration Testing Myths, Truths, & Best Practices
SynerComm partnered with ChannelBytes to present 60 minute session where we discuss what it means to do quality,...
SynerComm Reboots a Security Staple with ‘Continuous’ Pentesting
Participating in Black Hat USA 2020, we sat down with Dark Reading where our own Brian Judd, VP Information...
Incorporating Your Lessons Learned for Pandemic Contingency Planning Considerations
Although contingency planning has a healthy focus on technology, it still requires people to interface with that...
We’ll get through this; how will it make us stronger? Make COVID-19 “lessons learned” a priority
The COVID-19 event, obviously, has had a wide-reaching negative impact for the entire country. Despite this, even...
Building a Pwnagotchi
What is a Pwnagotchi? From the Website: Pwnagotchi is an A2C-based “AI” powered by bettercap and running on a...
Continuous Penetration Testing
“So, let’s say we fix all of the vulnerabilities that the pentest discovers… How do we know tomorrow that we’re...
People are People, but Where Can You Find Them When You Need Them?
Trying to find qualified IT infrastructure and security people? We at SynerComm help companies successfully...
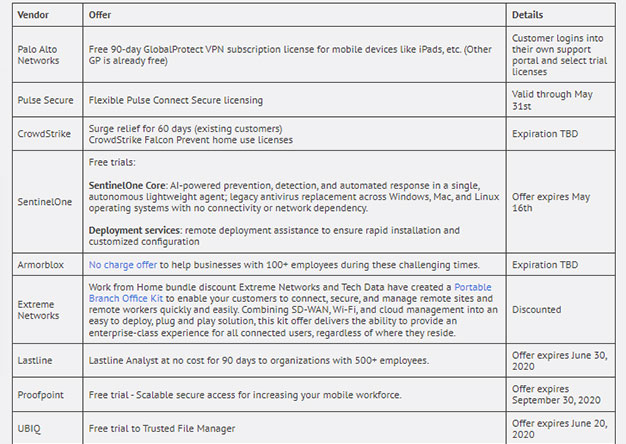
Vendors Stepping Up in a Time of Need
Most enterprises are getting slammed with employees working from home. Most of us designed our remote user VPN’s...
Remote Access Rush
Practicing good remote access hygiene in times of uncertainty As the business world reacts to the current health...
Are we prepared?
Risks and Considerations for IT: A Pandemic What can IT do to prepare? We all know the stats of the Coronavirus,...
Stop Sharing Your Password with Everyone
Insert under image - Palo Alto Networks firewalls have the ability to create security policies and generate logs...
Cybersecurity Maturity Model Certification (CMMC)
From a quick assessment on what has been published thus far on the CMMC regulation and its overall goal, it appears...
AWS Metadata Endpoint – How to Not Get Pwned like Capital One
One of the greatest yet unknown dangers that face any cloud-based application is the combination of an SSRF...
Understanding HIPAA: PHI and Covered Entities
Medical community challenge: In a business environment where resources are limited, compliance requirements abound,...
Understanding HIPAA: Starting with the Rules
Medical community challenge: In a business environment where resources are limited, compliance requirements abound,...
Why Microsoft Office 365 Secure Score Isn’t Enough
Microsoft Secure Score. If you’re an IT administrator or security professional in an organization that uses Office...
How to Approach the General Data Protection Regulation (GDPR) With a Security Framework
GDPR has been in place since May 25th, 2018 and has already been used in legal actions against companies, with over...
Framework or Crash, the Choice is Yours!
Are you using a framework to establish your information security program? If not, I get it; it’s complicated. On a...
Lessons Learned from Pentesting – What Should Keep You Up At Night
Coming from someone who can officially say that information security has given me a few gray hairs, I'm writing...
Characteristics of a Relevant Information Security Program: Communications
The Challenge You budget for, enable, and staff your organization’s information security program with people,...
Why 14 Characters?
Background While experts have agreed for decades that passwords are a weak method of authentication, their...
How to build a (2nd) 8 GPU password cracker
Why? … Stop asking questions! Background In February 2017, we took our first shot at upgrading our old...
DA 101 – Protecting your Domain Admin Account
At SynerComm's Fall IT Summit 2018 we presented a talk about the top 5 attacks used to compromise a Domain...
OpenSSH < 7.7 - Username Enumeration Exploit
On August 15th, 2018 a vulnerability was posted on the OSS-Security list. This post explained that OpenSSH (all...
Thoughts on Blocking Powershell.exe
This post is inspired by a twitter debate I observed between a pentester and a defender. It's characteristic of...
How to build a 8 GPU password cracker
TL;DR This build doesn't require any "black magic" or hours of frustration like desktop components do. If you...
The Upside Down – Ventures into the 5GHZ Spectrum
In the hit Netflix series 'Stranger Things', the Upside Down is the parallel dimension inhabited by a monster. It...
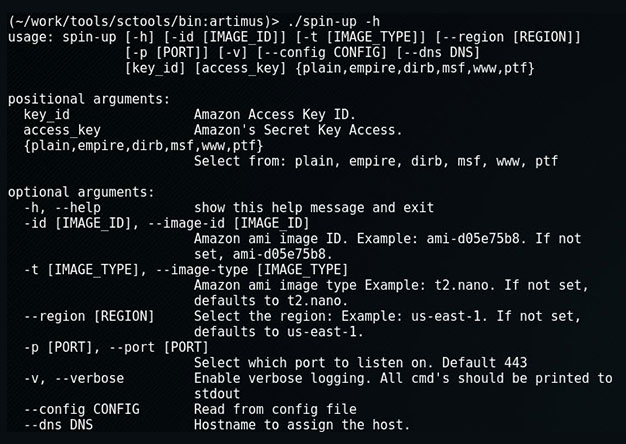
spin-up: Quickly Launch a Provisioned EC2 Attack Server
When on an engagement, sometimes we'll encounter an eager blue team hellbent on identify and blocking our attacks....
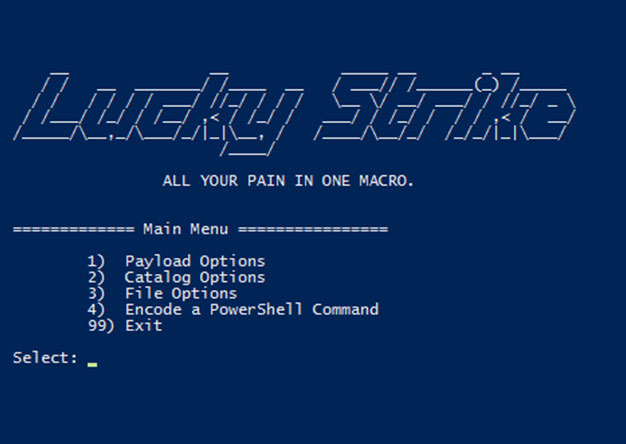
Luckystrike: An Evil Office Document Generator.
DerbyCon Tool Drop 2.0 Talk here. Luckystrike demo begins at 18:45. <tldr> Luckystrike is a PowerShell based...
The Number One Pentesting Tool You’re Not Using
TL;DR: Reporting sucks, rarely does anyone enjoy it. Serpico is a tool that helps with reporting and makes it suck...
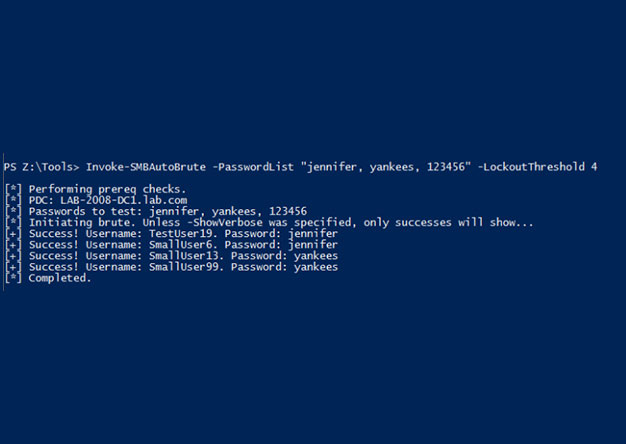
Invoke-SMBAutoBrute.ps1 – Smart SMB Brute Forcing
Intro One of my favorite post-ex metasploit modules is smb_login. It's great for running a quick test using...
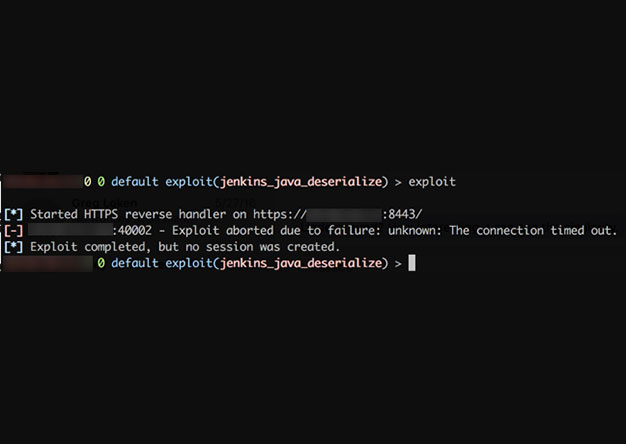
Weaponizing Nessus
Once in a blue moon we come across a client that has truly done security right (or at least, tried really hard to...
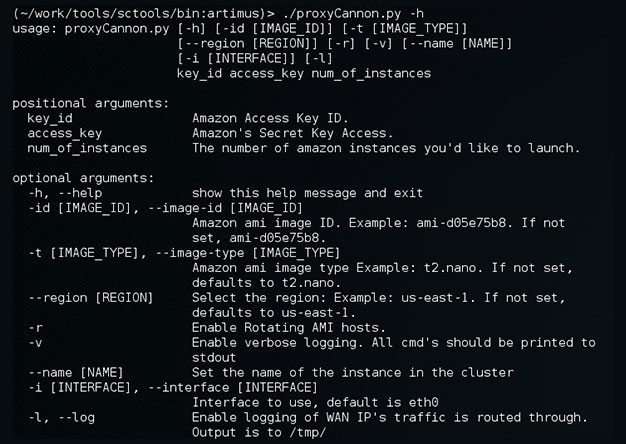
Update to ProxyCannon
ProxyCannon, which can be found here, has undergone some revisions since our initial release and as a result,...
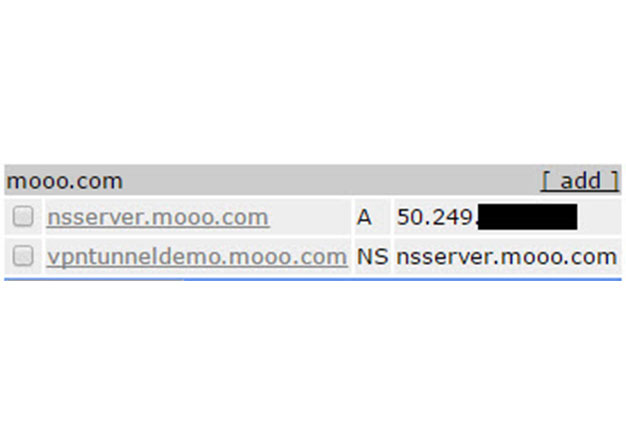
VPN over DNS
Overview For some time now, we've been using DNSCat as a means to covertly transmit data during engagements where...
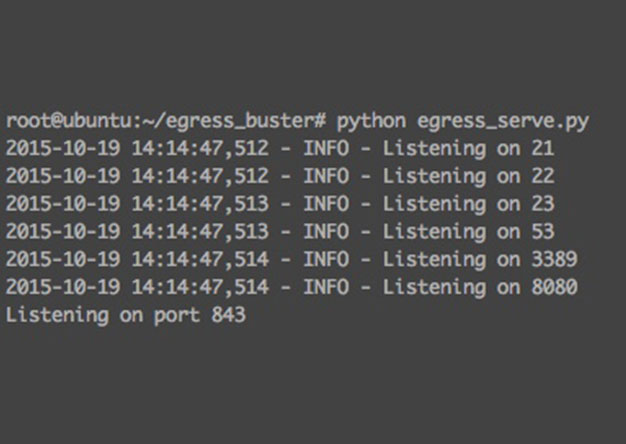
Websocket Based Egress Buster
Problem It is common during a penetration test that a tester may run into the problem of figuring out which ports...
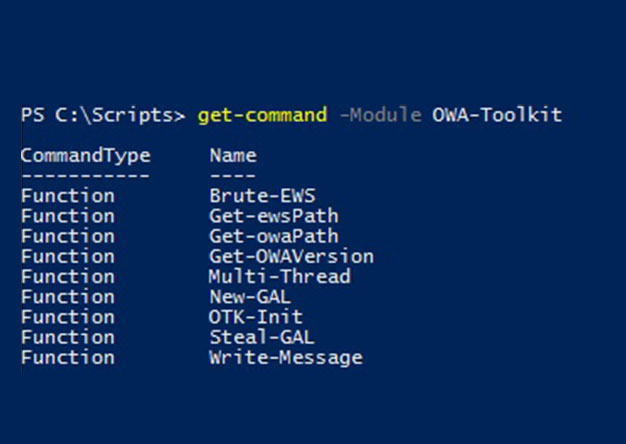
Abusing Exchange Web Service – Part 1
Outlook Web Access (OWA) has been one of the consistently viable attack vectors for pentesters and bad guys alike...
Why Security Awareness Training Fails
First, let's talk about what "failure" is and is not in the context of Security Awareness Training (SAT). Failure...
Assisted directory brute forcing
Very frequently during a web application assessment a pentester may begin by fingerprinting what web frameworks and...
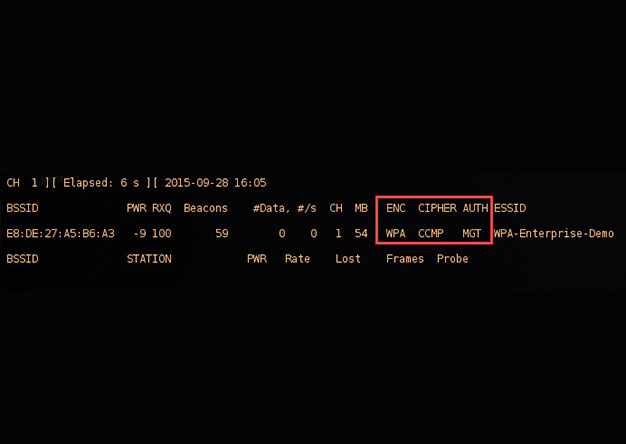
crEAP – Harvesting Users on Enterprise Wireless Networks
With the demands of a mobile workforce, wireless networks in enterprise environments are quite common. Typically,...
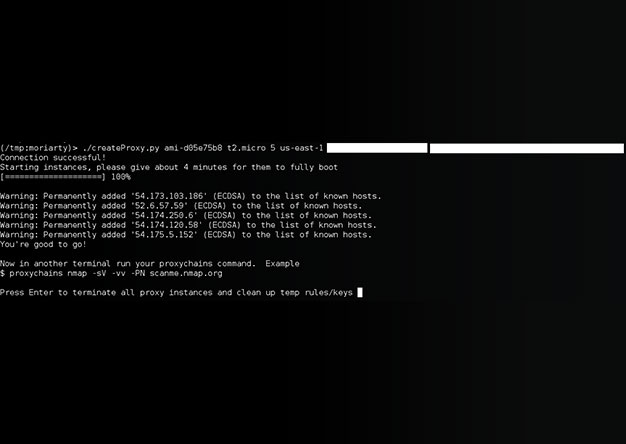
[UPDATE] Creating your own private botnet for scanning.
This is an update to an older post that can be found here. Since createProxy's initial release, we've received...
Drone Code Execution (Part 1)
Recently some of us here at shellntel have been building quadcopters and autonomous vehicles for fun. We are big...
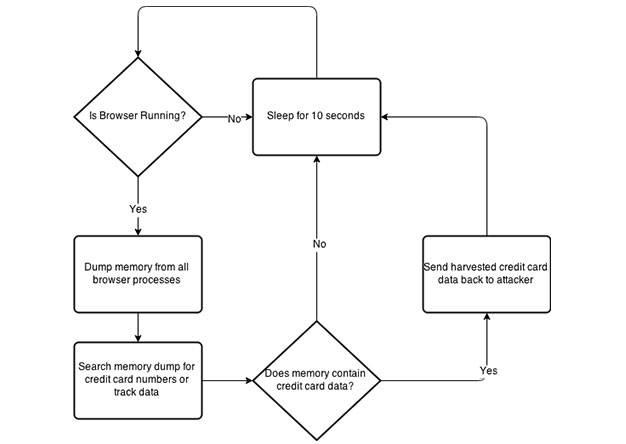
PowerShell Memory Scraping for Credit Cards
During the post exploitation phase of a penetration test, I like to provide the client with examples of what could...
Intro To Active Directory Delegation
One of the most frequent questions I get from my CircleCityCon/DerbyCon Active Directory talk goes something like...
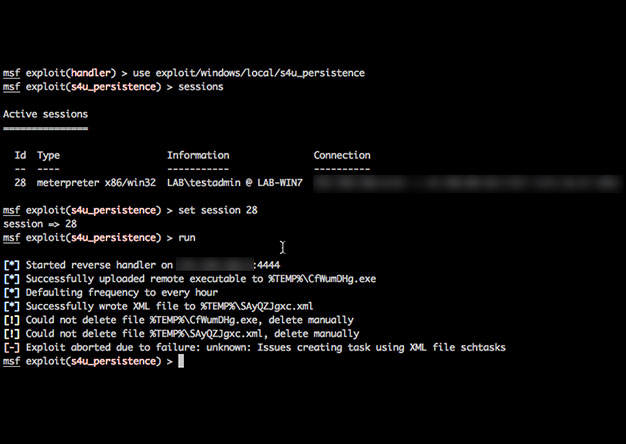
Using PowerShell & Unicorn to Get Persistence
Recently I was on an engagement where I received a meterpreter shell only to have it die within minutes before I...
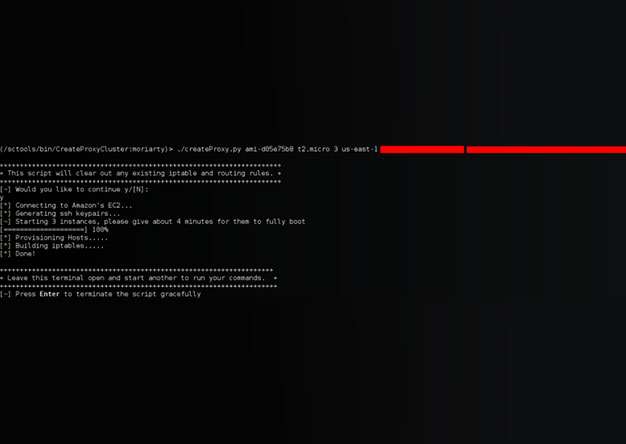
Creating your own private botnet for scanning.
[ UPDATE] The tool has been re-written. New details can be found here:...
Circle City Con: 2015 CTF Writeup
The shellntel team attended Circle City Con this year and participated in their second annual Capture The Flag...
Qualys Scanner API In Powershell Including External Ticket Creation
So you would like to automate your vulnerability management lifecycle? Good luck. But if you are motivated...
Validating the Effectiveness of Your Controls
About six years ago, social engineering penetration tests became the norm for the A-Team. In many of these tests,...
Dragon: A Windows, non-binding, passive download / exec backdoor
In my many years of participating in CCDC, I keep running into the same problem. If you've red teamed for one of...