Blog
Insights From Cybersecurity Experts

How to build a 8 GPU password cracker
TL;DR This build doesn't require any "black magic" or hours of frustration like desktop components do. If you follow this blog and its parts list, you'll have a working rig in 3 hours. These...

The Upside Down – Ventures into the 5GHZ Spectrum
In the hit Netflix series 'Stranger Things', the Upside Down is the parallel dimension inhabited by a monster. It is a dark and cold reflection of the dimension inhabited by humans, containing the...
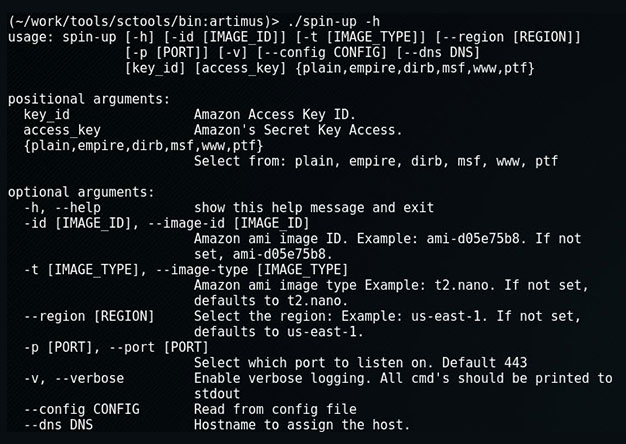
Spin-up: Quickly Launch a Provisioned EC2 Attack Server
When on an engagement, sometimes we'll encounter an eager blue team hellbent on identify and blocking our attacks. Typical in those instances we'd use proxy-cannon and route through multiple (ever...
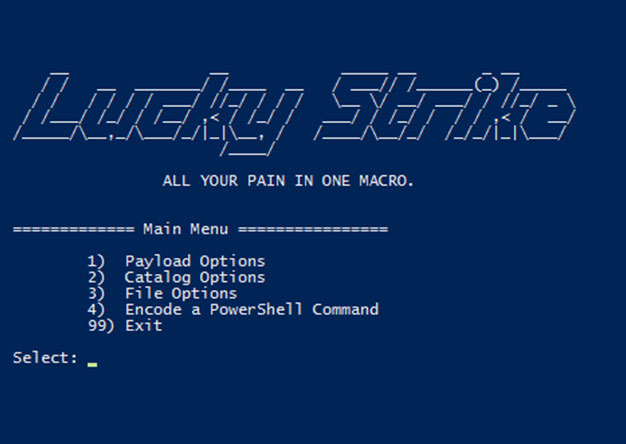
Luckystrike: An Evil Office Document Generator.
DerbyCon Tool Drop 2.0 Talk here. Luckystrike demo begins at 18:45. <tldr> Luckystrike is a PowerShell based generator of malicious .xls documents (soon to be .doc). All your payloads are...

The Number One Pentesting Tool You’re Not Using
TL;DR: Reporting sucks, rarely does anyone enjoy it. Serpico is a tool that helps with reporting and makes it suck less through collaboration and automation, saving you time that you’d rather spend...
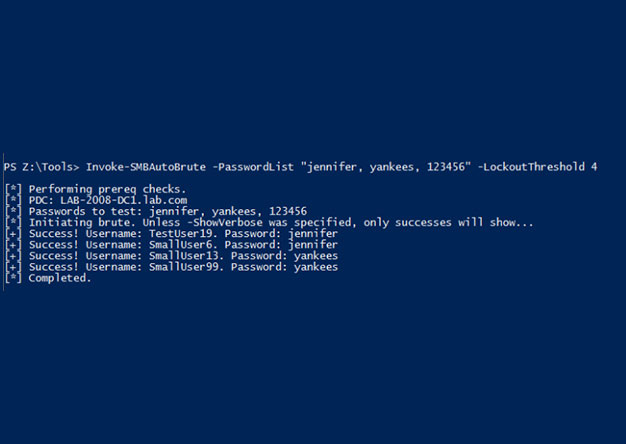
Invoke-SMBAutoBrute.ps1 – Smart SMB Brute Forcing
Intro One of my favorite post-ex metasploit modules is smb_login. It's great for running a quick test using credentials you've discovered. One of the problems with it is that there is nothing that...
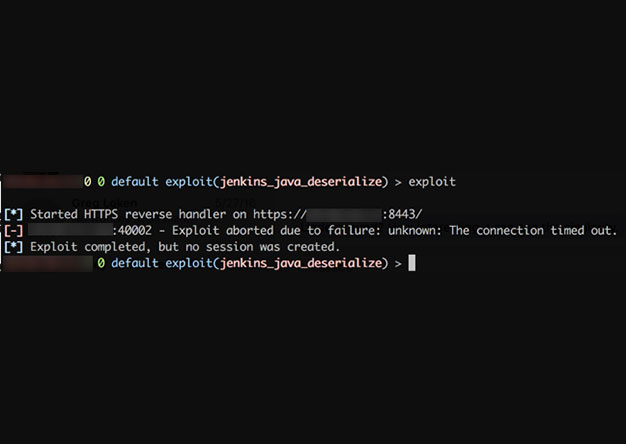
Weaponizing Nessus
Once in a blue moon we come across a client that has truly done security right (or at least, tried really hard to do so). All the low hanging fruit has been trimmed: Responder doesn't work, no...
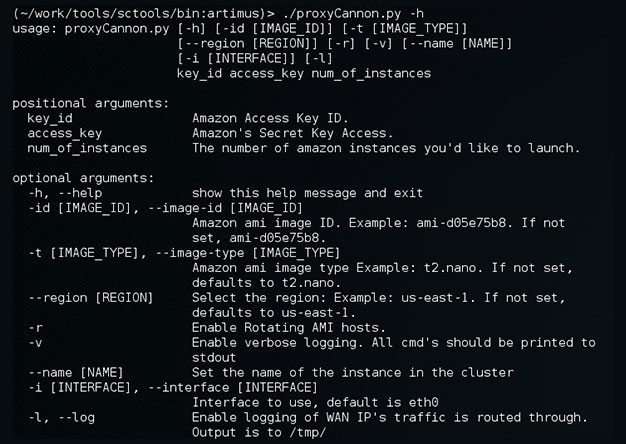
Update to ProxyCannon
ProxyCannon, which can be found here, has undergone some revisions since our initial release and as a result, there's some new features we'd like to introduce. Cleaner User Interface We've cleaned...
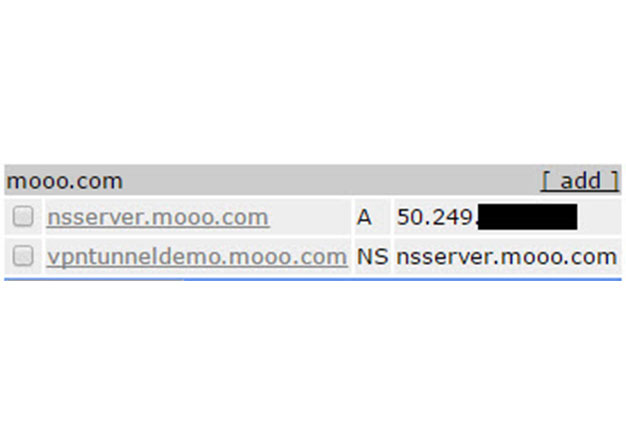
VPN over DNS
Overview For some time now, we've been using DNSCat as a means to covertly transmit data during engagements where clients IDS's or Firewalls might otherwise block us. The DNS protocol is often...
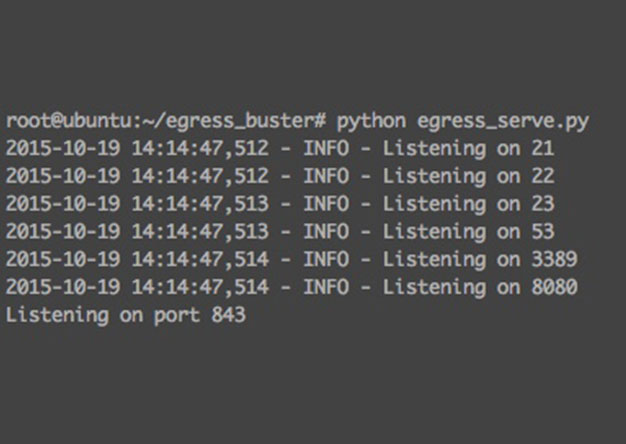
Websocket Based Egress Buster
Problem It is common during a penetration test that a tester may run into the problem of figuring out which ports and maybe even which protocols are allowed out of an environment. This is due to the...
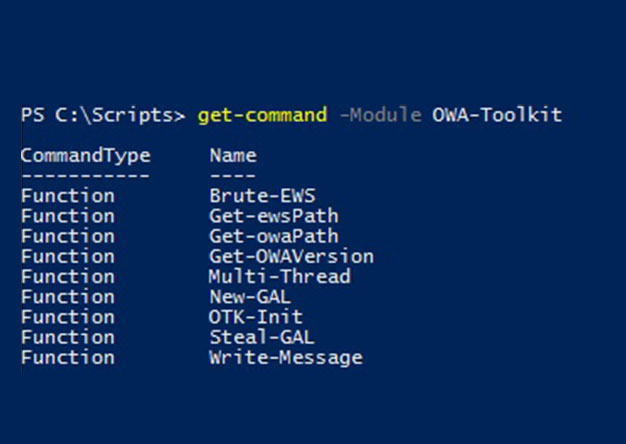
Abusing Exchange Web Service – Part 1
Outlook Web Access (OWA) has been one of the consistently viable attack vectors for pentesters and bad guys alike for many years. Frequently, an attacker will obtain valid credentials by brute...

Why Security Awareness Training Fails
First, let's talk about what "failure" is and is not in the context of Security Awareness Training (SAT). Failure is not when a company gets breached due to social engineering. Wait, what?? All the...

Assisted directory brute forcing
Very frequently during a web application assessment a pentester may begin by fingerprinting what web frameworks and libraries are used by a given application. Possibly by running a tool such as...
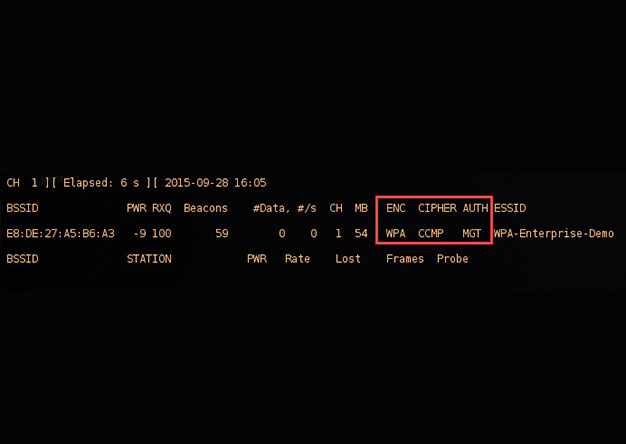
crEAP – Harvesting Users on Enterprise Wireless Networks
With the demands of a mobile workforce, wireless networks in enterprise environments are quite common. Typically, enterprise wireless networks employ WPA-Enterprise security features, which removes...
![[UPDATE] Creating your own private botnet for scanning.](https://www.synercomm.com/wp-content/uploads/2015/09/B87Im1.jpg)
[UPDATE] Creating your own private botnet for scanning.
This is an update to an older post that can be found here. Since createProxy's initial release, we've received some great feedback and, as a result, we made some improvements. There were several...

