DNS Security: The Internet’s Most Critical and Most Overlooked Attack Surface
The process of securing DNS is complicated because, unlike most other protocols, the principal purpose of DNS is to both publish information as well as allow clients to access that information. So, the methods we use to defend DNS, often have to stay away from the classic, simple blocking techniques.
Every digital interaction your organization relies on and begins the same way.
– A user opens an application.
– A system makes an API call.
– A cloud workload spins up.
Before anything else can happen, one quiet process must succeed, DNS.
The Domain Name System translates human-readable names into IP addresses, enabling communication across the internet and within enterprise networks. It is foundational. It is ubiquitous. And despite its importance, it remains one of the most underestimated components of modern cybersecurity strategies.
For CISOs focused on resilience, uptime, and trust, DNS security can no longer be an afterthought.
Why DNS Matters More Than You Think
DNS sits at the intersection of availability, integrity, and confidentiality (CIA). Every external-facing service and nearly every internal application depends on it.
If DNS fails, or worse, is manipulated, your users cannot connect, your applications cannot communicate, users may be directed to a promised server to harvest authentication or data, and your security controls may never see the attack coming.
Yet many organizations treat DNS as “plumbing,” something that just works until it doesn’t.
Attackers don’t share that view.
They understand that DNS is often trusted implicitly, monitored minimally, and protected inconsistently. That makes it an ideal target.
A Legacy Protocol in a Modern Threat Landscape
DNS was designed in the 1980s for speed and scalability, not for today’s hostile, zero-trust world. It lacks native encryption and strong authentication, leaving it vulnerable to interception, spoofing, and abuse.
Over the years, defenders have layered security tools around DNS, but the protocol itself still presents opportunities for adversaries to redirect traffic without triggering traditional security controls, exfiltrate data through covert DNS channels, or disrupt availability at massive scale.
Understanding Where DNS Is Vulnerable
A typical DNS lookup traverses multiple systems, including local caches, recursive resolvers, root servers, top-level domains, and authoritative name servers. Each step introduces potential weaknesses.
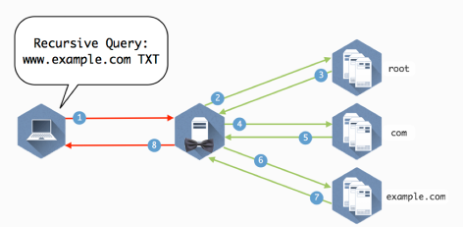
Recursive DNS Servers
These are frequent targets due to their exposure and central role. Common risks include:
– Cache poisoning and spoofing
– DDoS amplification
– Open recursion misconfigurations
– DNS-based data exfiltration
Authoritative DNS Servers
These systems define how your domains resolve and what users ultimately reach. They are vulnerable to:
– DDoS attacks
– DNS hijacking
– Misconfigured zone transfers
“Sitting ducks” delegation issues that leave domains exposed even when infrastructure changes
Firewalls alone are not enough to protect these systems. DNS requires security controls that understand the protocol itself.
DNS Attack Techniques CISOs Must Address:
DNS Spoofing and Cache Poisoning
Attackers inject malicious responses into DNS caches, redirecting users to fraudulent destinations. Without protections like DNSSEC and hardened resolvers, users have no way to verify authenticity.
DNS Tunneling and Data Exfiltration
DNS can be abused as a covert communication channel. Because DNS traffic is often allowed through firewalls by default, attackers encode data into queries and responses, bypassing perimeter defenses entirely.
DNS-Based DDoS Attacks
DNS infrastructure can be overwhelmed directly or abused for amplification attacks, impacting availability at scale. Without redundancy, rate limiting, and intelligent traffic inspection, organizations risk widespread outages.
A Layered Approach to DNS Security
Effective DNS security is not a single product; it is an architecture.
This DNS architecture is now exponentially more complicated with:
– Internal DNS
– External DNS
– Cloud specific DNS.
Many cloud DNS infrastructures overlap with onprem DNS, giving inconsistent query responses and increase troubleshooting
Many cloud DNS security offerings pale in comparison to Enterprise DNS solutions, increasing risk
Operational nightmare maintaining and securing disparate systems.
At the root of it (no pun intended) DNS security is fundamentally two-fold: protecting the DNS infrastructure (servers and resolution process) from attacks like spoofing and DDoS and protecting the data integrity and privacy of DNS queries, ensuring users are sent to the correct, safe websites and not malicious ones.
Building a Layered DNS Defense
Protecting the Server (Infrastructure)
- Eliminate server/OS/Application Vulnerabilities: Harden DNS operating systems and software
- Segment DNS infrastructure: Better visibility and control with DNS Servers isolated and traversing a firewall from general-purpose systems. Firewalls add DDos protection.
- Distribute DNS services to eliminate single points of failure.
Protecting the Data (Queries & Responses)
- DNSSEC (DNS Security Extensions): Adds digital signatures to DNS data, verifying its authenticity and preventing tampering, ensuring data integrity.
- Protective DNS (PDNS) is any security service that analyzes DNS queries and takes action to mitigate threats: Prevents access to malware, ransomware, phishing attacks, viruses, malicious sites, and spyware at the source, making the network inherently more secure.
- Encryption (DoT/DoH): DNS over TLS (DoT) and DNS over HTTPS (DoH) encrypt DNS queries between the user and resolver, preventing eavesdropping and man-in-the-middle attacks.
- Restrict Zone Transfers & Data Integrity: Ensures the response received is the one originally sent, preventing malicious alteration.
- Monitor Query Response Transactions for anomalies. DNS telemetry is one of the earliest indicators of compromise, but only if you’re looking
Control Dynamic Updates
- Use secure update mechanisms via GSS-TSIG: Ensure internal devices are Domain authenticated.
- Enable scavenging: To reduce stale records
- Review logs: Regularly for unauthorized changes
Practice Strong Security Hygiene
- Maintain clear DNS documentation
- Back up zone data
- Enforce RBAC, MFA, and strong credentials
- Train administrators on DNS-specific risks
- Conduct regular audits and configuration reviews
The CISO Takeaway
DNS is not “just networking.” It is a control plane of trust.
Understanding your Enterprise DNS is critical part of your security program.
External DNS: Starting with your Domain portfolio management (Registered Domain, expirations dates, sub domain registration, Domain record management exposing risky data) to External DNS server and data protection, Domain monitoring to protect your business and customers from high jacking to ongoing monitoring.
Internal DNS: Resiliency, protective DNS subscriptions to protect users from malware and data exfiltration and scavenging of stale records.
For CISOs focused on resilience, business continuity, and risk reduction, securing DNS is a strategic priority
Call to Action:
Audit your DNS environment today. Eliminate DNS risks, enforce documentation, and integrate DNS telemetry into your SOC.
Partner with your security team and our trusted advisors to build a layered DNS defense.
Author: Lisa Niles, CISSP