Turning Password Data into Meaningful Insight
Our consultants often spend time helping organizations better understand concerning truths about their environments. Password hygiene continues to be a frequent and easily exploited weakness in pentesting. Over time, that reality pushed us to invest not only in better cracking infrastructure, but in something just as important, better analysis and better reporting. The result of that effort is Hash Master 1000.
Hash Master 1000 started as an internal project. Like many consulting teams, we had strong cracking capabilities and experienced testers, but turning cracked password data into consistent, meaningful insight took time. Analysts were manually correlating results, normalizing data across assessments, and assembling reports using a mix of scripts, spreadsheets, and screenshots. The work got done, but it wasn’t as efficient as it could be.
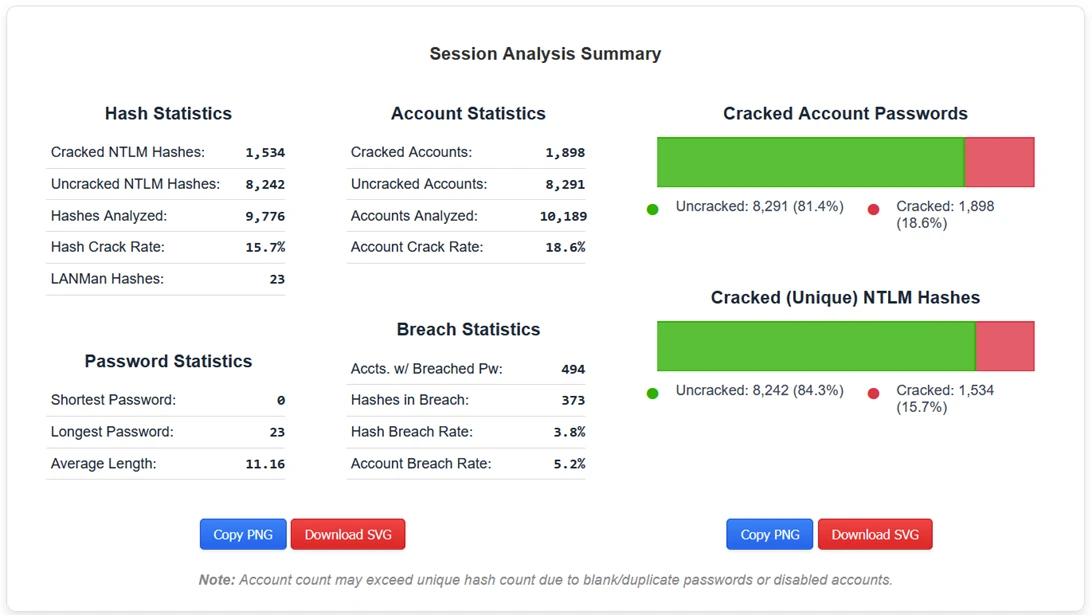
Actual 1-Click Exportable Report from Hash Master 1000
The goal behind Hash Master 1000 was simple, take the results of an Active Directory password assessment and turn them into clear, repeatable, defensible findings. Not just “here are the most common passwords,” but answers to the questions that actually matter:
- How widespread is password reuse?
- Where are policy failures occurring?
- Which accounts represent excessive risk?
- How has password hygiene changed over time?
Hash Master 1000 v2.0 Workflow
With version 2.0, Hash Master 1000 has grown into a mature workflow. The application guides analysts through validation, configuration, and reporting, supports session management for multi-project environments, and enables historical trend analysis across assessments.
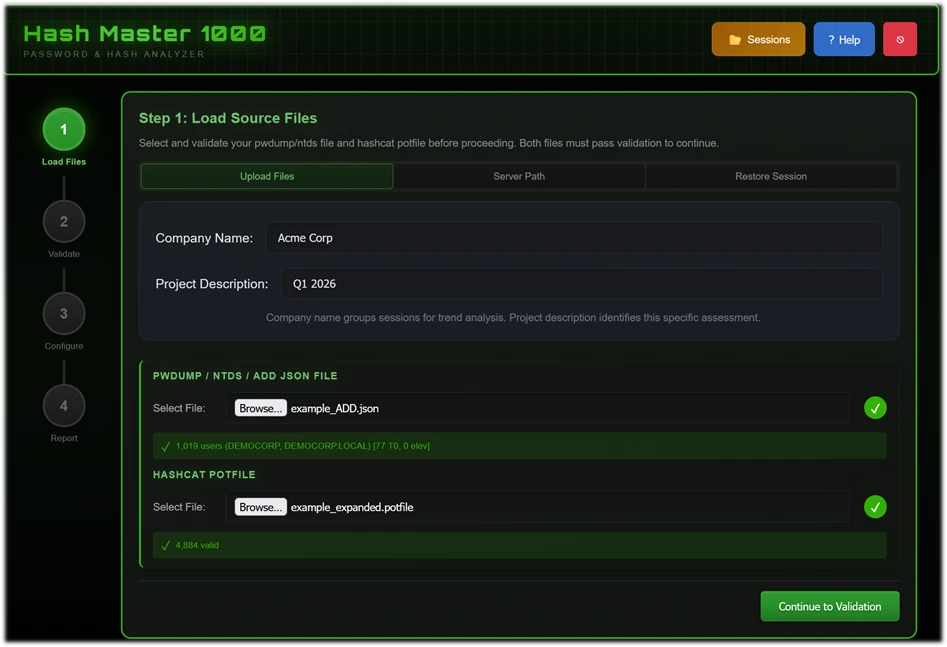
Step 1: Import Hashes & Hashcat Potfile
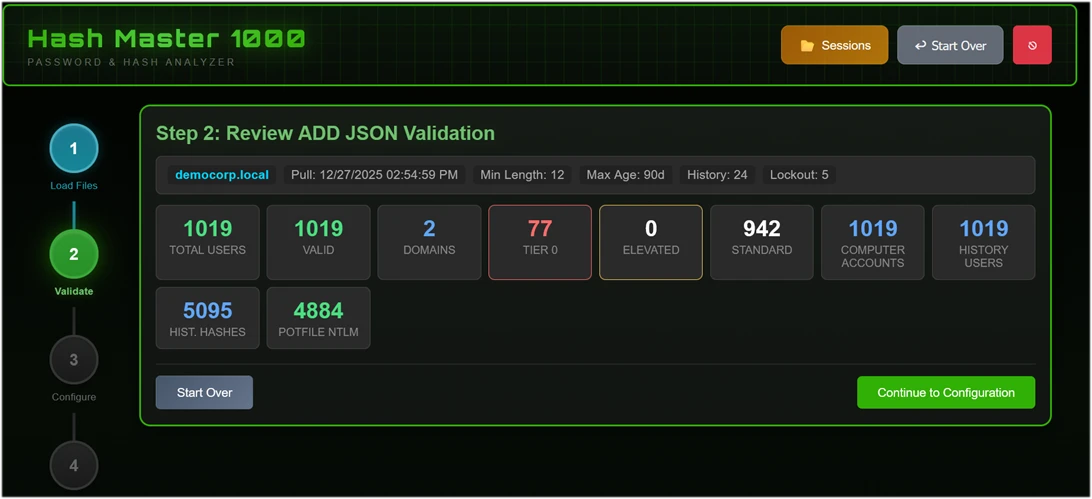
Step 2: Validate Accounts & Hashes
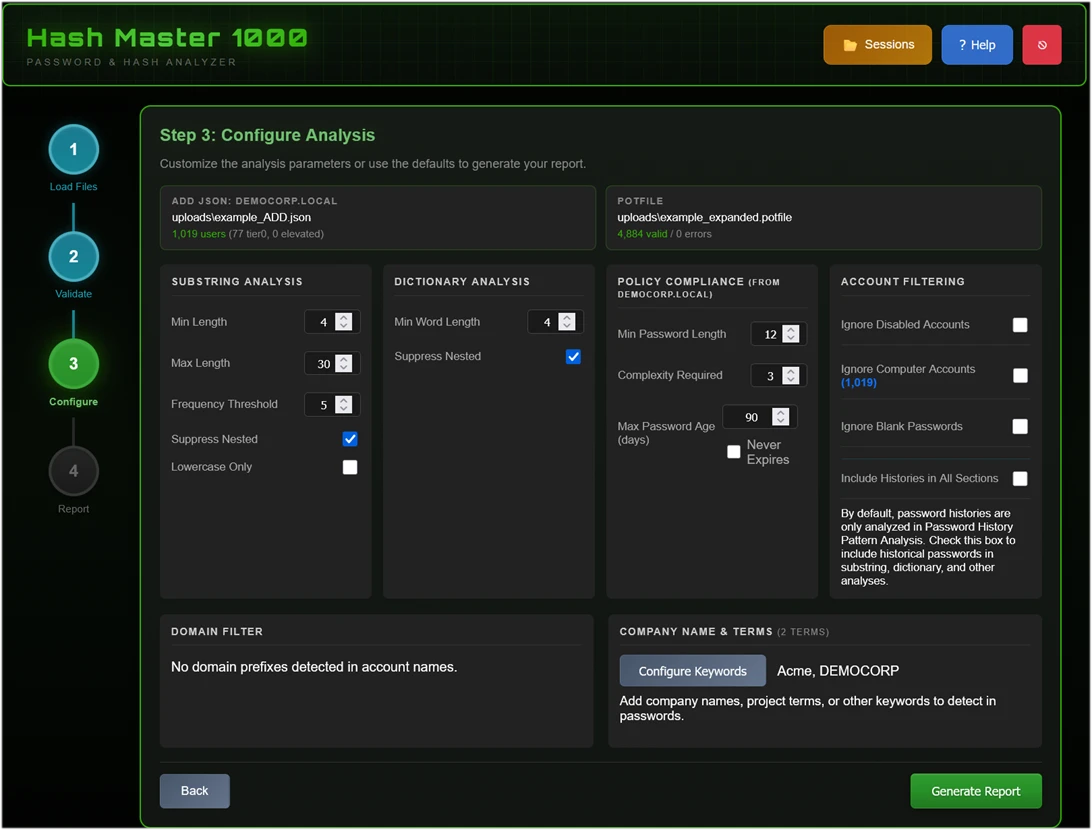
Step 3: Configure Analysis Options
Step 4: Analysis and Reports
Hash Master 1000 v2.0 has 20+ New Features
Hash Master 1000 v2.0 now incorporates Active Directory–aware analysis, including Kerberoast and AS-REP exposure, password history evaluation, account description disclosure checks, Group Policy membership, User Account Control settings, and accurate detection of computer accounts. All reporting is visual, exportable, and designed to be understandable by both technical and non-technical audiences.
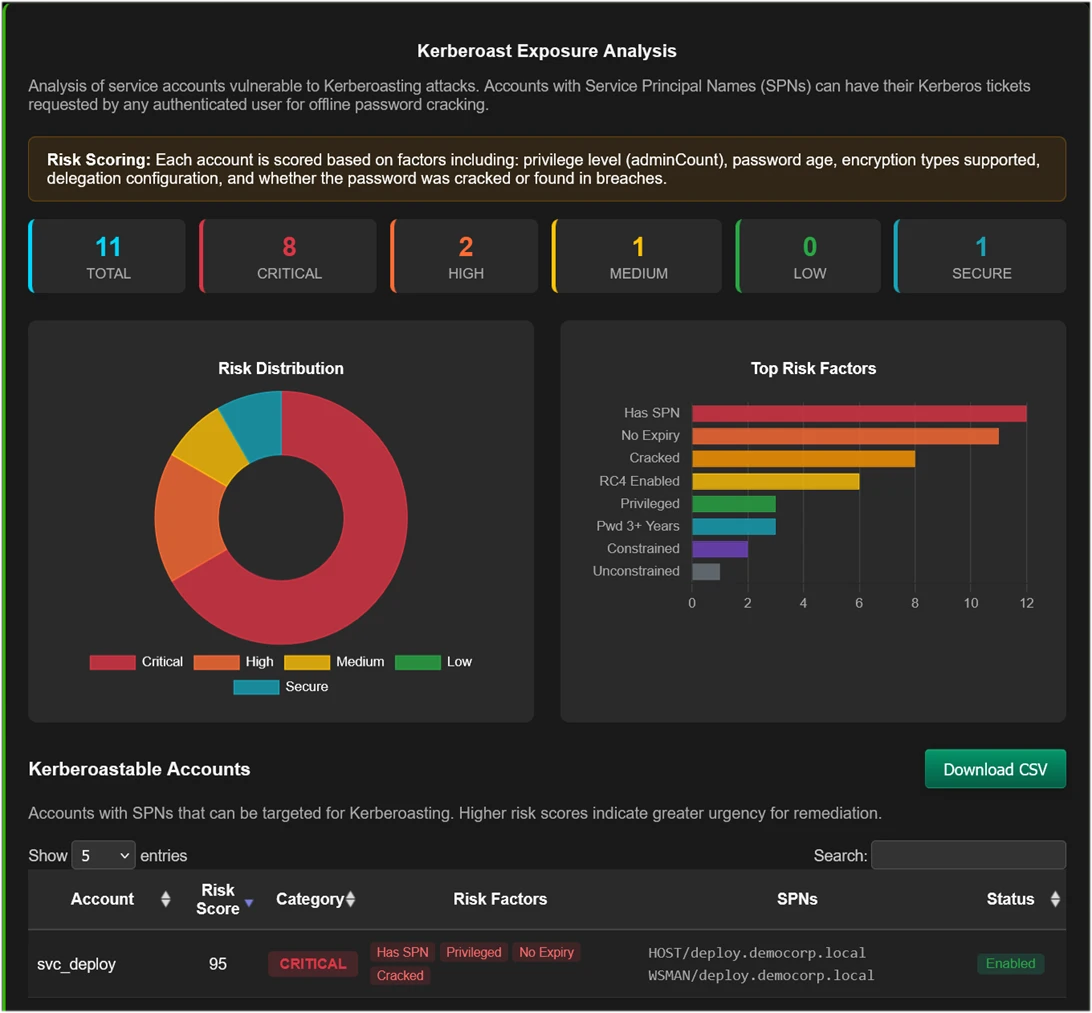
Hash Master 1000 v2.0: Kerberoast Exposure Report
Version 2.0 also introduces an experimental but powerful capability, Advanced AI Analysis (AAIA). Using local, privately controlled AI models, Hash Master 1000 v2.0 can assist analysts by identifying patterns, summarizing risk, and helping draft narrative findings. This is not a replacement for human expertise, and it is intentionally designed with caution and transparency. Even in its early form, however, it is already demonstrating how AI will play an important role in the future of password and hash analysis and reporting.
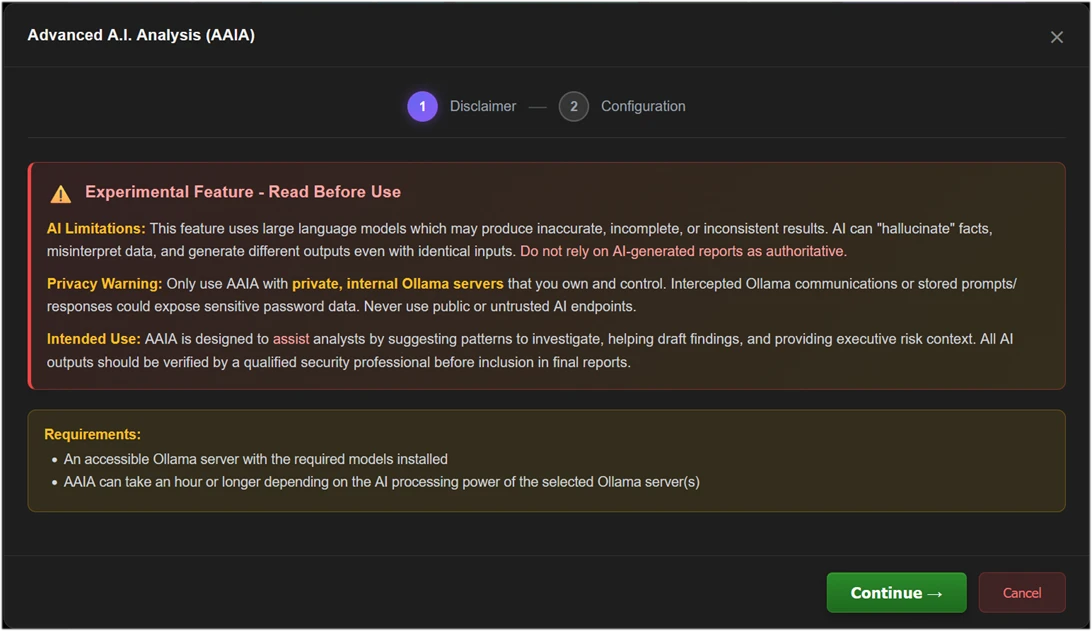
Advanced AI Analysis – Privacy is Required
Another exciting new feature is allowing users to compare both cracked and uncracked hashes against the latest Have I Been Pwned (HIBP) database of breached passwords and password hashes. HIBP allows hashes to be compared anonymously against a live online database of passwords already known to attackers. Of course, the best practice is to prevent (when possible) and disallow the use of passwords appearing in known breaches.
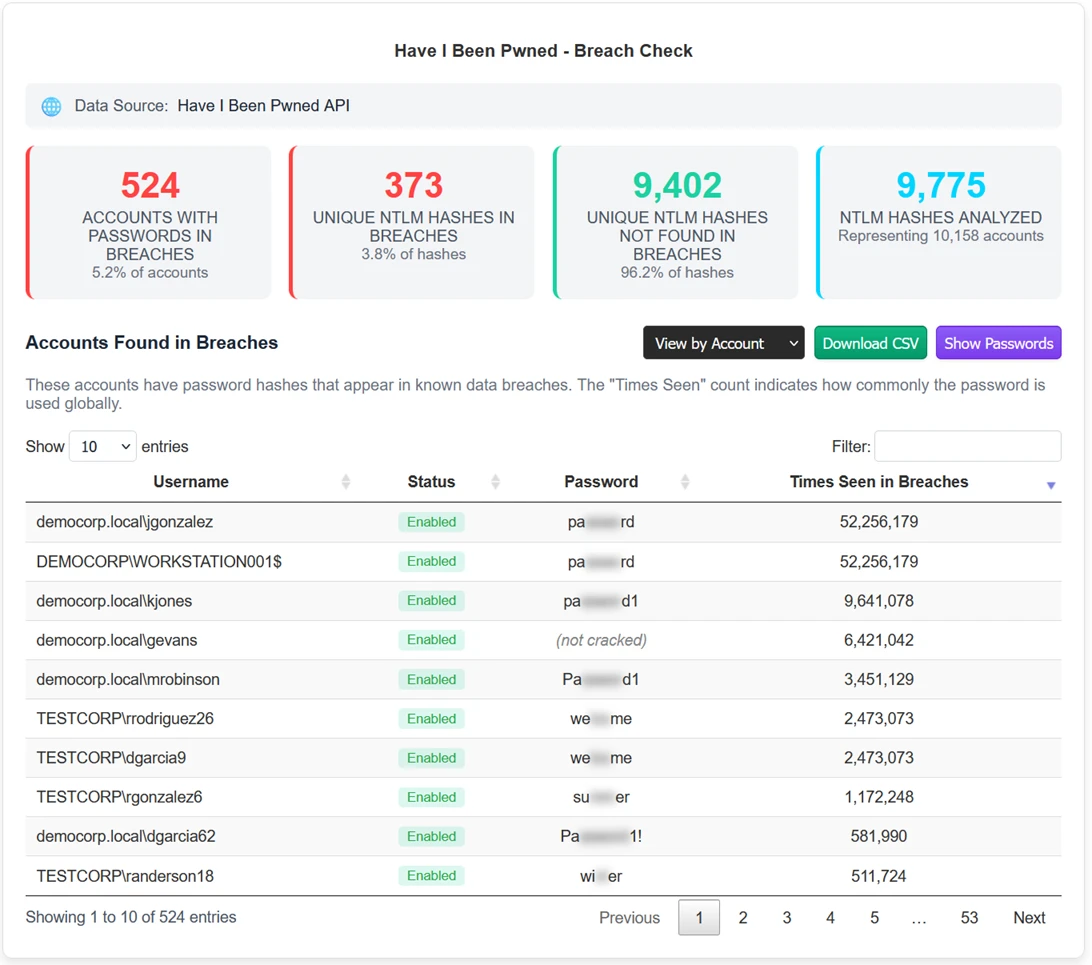
Breach Check Report: Anonymously compare NT hashes to Have I Been Pwned
Hash Master 1000 v2.0 is Free
What’s best is that Hash Master 1000 is released for free. That decision was intentional. Better tools raise the overall quality of security assessments, and when the community benefits, everyone benefits. Releasing the tool publicly also invites feedback, review, and improvement, which ultimately makes the tool stronger.
At the same time, it’s important to be clear about what Hash Master 1000 is and is not. Password and hash analysis is only half the battle. Meaningful results still depend on the ability to crack hashes effectively. At SynerComm, we continue to invest heavily in powerful cracking infrastructure and optimized workflows. Hash Master 1000 does not replace that investment, it amplifies it by ensuring the results are fully understood and communicated.
Hash Master 1000 reflects how we approach security at SynerComm, practical, transparent, and grounded in real-world testing. Version 2.0 represents a significant milestone in that journey, and we’re proud to share it with the community.



