Trying to find qualified IT infrastructure and security people? We at SynerComm help companies successfully overcome that challenge every day, and so I suppose I suffer from the old adage: “to a...

Insights From Cybersecurity Experts

Trying to find qualified IT infrastructure and security people? We at SynerComm help companies successfully overcome that challenge every day, and so I suppose I suffer from the old adage: “to a...
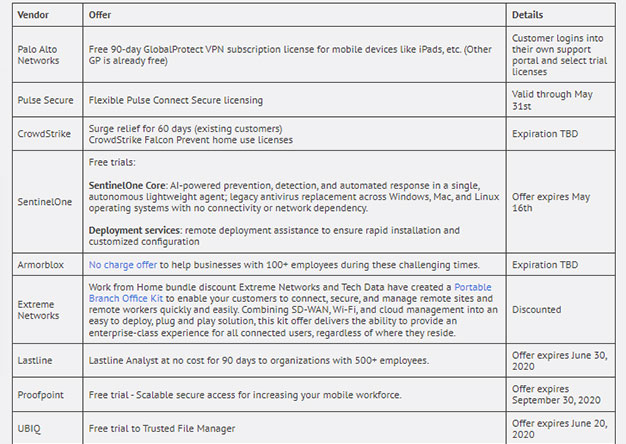
Most enterprises are getting slammed with employees working from home. Most of us designed our remote user VPN’s for the occasional "snow day" ...right. Now we have an entire workforce, working from...
Practicing good remote access hygiene in times of uncertainty As the business world reacts to the current health crisis, companies are offering remote access to any role that can work from home....
Risks and Considerations for IT: A Pandemic What can IT do to prepare? We all know the stats of the Coronavirus, although they are changing by the minute. We know what to do personally and for our...
From a quick assessment on what has been published thus far on the CMMC regulation and its overall goal, it appears that contractors lack of information security will no longer be tolerated by the...
Medical community challenge: In a business environment where resources are limited, compliance requirements abound, and budgets are constantly challenged to meet cost containment targets, the...
Medical community challenge: In a business environment where resources are limited, compliance requirements abound, and budgets are constantly struggling to meet cost containment targets, the...
Microsoft Secure Score. If you’re an IT administrator or security professional in an organization that uses Office 365, then you’ve no doubt used the tool or at least heard the term. It started as...
Are you using a framework to establish your information security program? If not, I get it; it’s complicated. On a second thought, have you lost your mind? I’ve been there. A number of years ago,...
Coming from someone who can officially say that information security has given me a few gray hairs, I'm writing this article from the perspective of someone who's been around the block. With over 15...