Security teams rely heavily on reputation-based threat intelligence to block malicious traffic. These controls are effective at shutting down known command-and-control servers, botnet servers, Tor...

Insights From Cybersecurity Experts

Security teams rely heavily on reputation-based threat intelligence to block malicious traffic. These controls are effective at shutting down known command-and-control servers, botnet servers, Tor...
A look into what the SOC process was designed for and how to determine if it is something you need.

See the original publication found in On Balance Magazine. At some point in 2015, cybercriminals had an aha moment. Instead of going through all of the trouble of breaking into a network, stealing...

Another M365 email outage... seriously just Google it... there are even multiple websites that monitor and tell you there is an outage but there is nothing you can do about it… or is there? Whether...
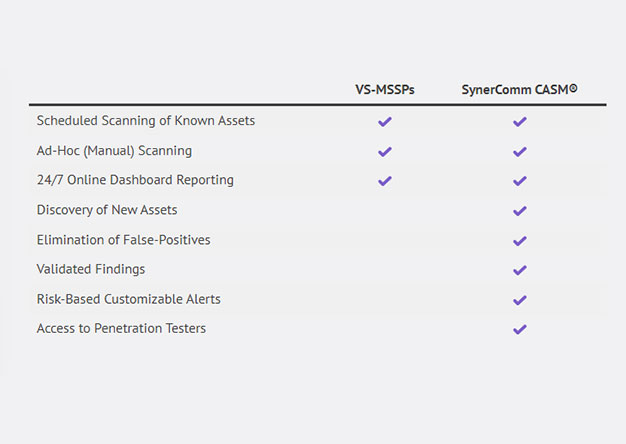
Warning: This blog contains purposeful marketing and gratuitous plugs for SynerComm’s CASM™ Subscription services. Seriously though, the following article will present the need for better external...

One of the things I have noticed while working at SynerComm over the years is that while most companies have employees on staff who possess the necessary technical knowledge to complete their...
The COVID-19 event, obviously, has had a wide-reaching negative impact for the entire country. Despite this, even in the face of the trauma linked to the loss of loved ones, we will eventually...

“So, let’s say we fix all of the vulnerabilities that the pentest discovers… How do we know tomorrow that we’re not vulnerable to something new?” ~Customer Bridging the Gap Between...

Trying to find qualified IT infrastructure and security people? We at SynerComm help companies successfully overcome that challenge every day, and so I suppose I suffer from the old adage: “to a...
Practicing good remote access hygiene in times of uncertainty As the business world reacts to the current health crisis, companies are offering remote access to any role that can work from home....