Over the past 20-years, I’ve used every major vulnerability scanner. There are several great scanners on the market, and SynerComm has continually used one of them from its free GNU public license years (pre-Oct. 2005), to its current version today. As the tactics, techniques, and procedures (TTP) of cyber-criminals evolved, our testing methodologies also adapted to meet the latest threats. What was possibly the only tool in most tool-kits 20 years ago, is now just one of many.
By today’s standards, running and reviewing a daily or weekly vulnerability scan should be the minimal starting point for basic perimeter security. Even though scanners continually add checks for new threats, they can’t check for everything. In fact, they often miss the most critical vulnerabilities and give security personnel a false sense of security.
Vulnerability scanning is undoubtedly a valuable tool for identifying known vulnerabilities within an organization's network and systems. The key word being “known”. Scanning involves the automated detection of weaknesses such as outdated software, misconfigurations, and unpatched systems through the use of special network probes. As useful as vulnerability scanning is, it’s essential to recognize its limitations.
Vulnerability scanning tools rely on databases of known vulnerabilities to identify weaknesses within an organization's network and systems. While effective at detecting vulnerabilities with published patches or fixes, these tools can't identify zero-day vulnerabilities or emerging threats that have not yet been documented. This limitation leaves organizations vulnerable to attacks exploiting unknown weaknesses, as vulnerability scanners lack the capability to predict or detect novel attack vectors.
Many organizations rely on custom-built/proprietary applications and APIs to support their business operations. These applications contain unique features and functionalities that vulnerability scanning tools may not fully understand or be able to assess accurately. As a result, vulnerabilities specific to custom applications, such as logic flaws or poor input sanitization, will likely go undetected by vulnerability scanners.
Weak passwords and lacking multi-factor authentication (MFA) both represent significant security risks for organizations. In fact, when combined it really doesn’t get much worse. Many scanners provide an option to test blank or default passwords, but none will find users with weak passwords or validate that MFA is properly configured. Consequently, weak authentication mechanisms remain one of the most exploited vulnerabilities, despite being so well-known.
Vulnerability scanning tools operate within the confines of the targets or assets specified by the organization, scanning only the systems and networks explicitly designated for evaluation. Scanners lack the ability to discover previously unknown assets or identify shadow IT resources that may exist outside the organization's visibility. This limitation leaves organizations vulnerable to unmonitored or unmanaged assets that could serve as potential entry points for attackers, bypassing the organization's perimeter defenses undetected.
Vulnerability scanning tools provide a snapshot of the security posture at a specific point in time, but they lack the contextual understanding necessary to assess the exploitability or potential impact of the identified vulnerabilities. They may also generate false positives which leads to alert fatigue and diverting resources away from genuine threats. Without human intervention to validate and prioritize vulnerabilities based on their relevance and potential impact on business operations, organizations risk overlooking critical security flaws.
Vulnerability scanning tools often rely on banners and other disclosures to identify software versions so they can be compared to a vulnerability database. Even when a scanner uses an exploit to check for a vulnerability, it still lacks the capability to mimic the sophisticated tactics and techniques employed by real-world attackers. On the other hand, penetration testing emulates actual cyber-attacks to assess the effectiveness of security controls and incident response procedures. Vulnerability scanning tools can only provide limited insights into how attackers might identify and exploit vulnerabilities.
While vulnerability scanning serves a crucial cybersecurity function, it’s far from being comprehensive or sufficient on its own. Perimeter vulnerability management has evolved into what Gartner describes as External Attack Surface Management (EASM), and the traditional vulnerability scanner should now be part of broader more encompassing platforms. Automated asset discovery, continuous vulnerability scanning, web service and API testing, and penetration testing should all be considered in a modern perimeter security strategy.
Penetration testing, also known as ethical hacking, goes beyond vulnerability scanning by simulating real-world cyber attacks to assess the resilience of an organization's defenses. Unlike vulnerability scanning, which only focuses on identifying weaknesses, penetration testing also evaluates the exploitability of vulnerabilities and the effectiveness of security controls in place. This includes testing for vulnerabilities that scanners are not programmed for or able to detect.
By emulating the tactics and techniques employed by malicious actors, penetration testers uncover vulnerabilities that may not be detected by automated scanning tools. They assess the entire attack surface, including network infrastructure, applications, and human factors, to identify potential entry points and security gaps.
Moreover, penetration testing provides valuable insights into the impact of successful attacks, helping organizations prioritize remediation efforts based on the severity and potential consequences of identified vulnerabilities. It also enables organizations to test incident response procedures and evaluate the effectiveness of security controls in mitigating or containing breaches. A modern example is that penetration testing is an excellent measure of an organization’s susceptibility to ransomware while vulnerability scanning provides very few useful insights.
In addition to infrastructure vulnerabilities, applications represent a significant attack vector for cybercriminals. Application assessments and code reviews play a vital role in identifying security flaws and weaknesses within custom-coded or third-party developed applications.
Application assessments involve analyzing the security architecture, design, and implementation of web and mobile applications to identify vulnerabilities such as injection flaws, authentication bypasses, and sensitive data exposures. Dynamic application testing refers to testing a live running application in an environment similar or identical to it’s intended production use. Dynamic assessments not only test for and verify the presence of vulnerabilities, but they also attempt to bypass protective controls. Code reviews allow the assessor to examine the source code to uncover logic errors, backdoors, and other vulnerabilities that may not be apparent through dynamic testing alone. Code reviews also allow the pentester to show developers exactly where and why vulnerabilities exist.
By conducting application assessments and code reviews, organizations can identify and remediate vulnerabilities early in the development lifecycle, reducing the risk of deploying insecure applications into production environments. This proactive approach helps organizations build robust and resilient applications that withstand potential attacks.
Organizations have expanded their networks and systems well beyond traditional perimeter boundaries. Today’s external assets include cloud services, third-party SaaS, and digital assets hosted by external providers. External attack surface management tools help organizations gain visibility into their entire attack surface and identify potential security risks stemming from previously unknown exposures.
EASM platforms combine dozens of techniques such as passive reconnaissance, digital footprinting, vulnerability scanning, and most importantly, asset discovery. EASM is designed to discover and map out an organization's entire external-facing infrastructure and assets. By monitoring changes to the attack surface and identifying misconfigurations or vulnerabilities, these tools enable organizations to proactively defend against external threats and prevent unauthorized access to sensitive data or systems.
While vulnerability scanning serves as a foundational element of cybersecurity, it is insufficient on its own and can’t provide comprehensive perimeter vulnerability detection. Adversaries are continuously evolving their tactics and targeting organizations with increasing sophistication. Additional measures such as penetration testing, application assessments and code reviews, and external attack surface management are all essential tools for bolstering defenses and preventing breaches.
By adopting a holistic approach to cybersecurity that combines automated scanning tools with human expertise and specialized assessments, organizations can strengthen their resilience to cyber threats and mitigate the risk of costly data breaches and disruptions to business operations. In a world where the stakes have never been higher, investing in proactive security measures is not just a choice but a necessity for business survival.
Are you looking for a pentest? A continuous pentest? Or maybe attack surface management? We’ll never have a shortage of new terminology (and acronyms) to learn and understand. When evaluating security vendors and comparing their solutions, it’s critical that everyone is on the same page and speaking the same language. This article starts to shed light on several key terms in hopes of offering clarity and understanding. So, let’s call this Part 1 of the continuous pentest cybersecurity glossary.
1. Continuous Threat Exposure Management (CTEM)
Continuous Threat Exposure Management (CTEM) refers to the ongoing process of identifying, assessing, and mitigating risks associated with potential threats to an organization's assets and infrastructure. CTEM involves continuous monitoring and analysis of various attack vectors and vulnerabilities to maintain an up-to-date understanding of the threat landscape. This proactive approach enables organizations to swiftly respond to emerging threats and fortify their defenses.
2. Attack Surface Management (ASM)
Attack Surface Management (ASM) encompasses the process of identifying and monitoring all potential entry points (attack surfaces) that malicious actors could use to infiltrate an organization's networks or systems. ASM solutions help organizations gain visibility into their digital footprint, assess associated risks, and implement effective controls to reduce the attack surface and enhance their overall security posture. Most ASM platforms are cloud-based and only provide visibility into public-facing assets, making them External Attack Surface Management (EASM) solutions.
3. Cyber Asset Attack Surface Management (CAASM)
Cyber Asset Attack Surface Management (CAASM) focuses specifically on managing the attack surface of an organization’s external and internal digital assets. This includes devices, endpoints, applications, and cloud resources. CAASM solutions usually receive information through API integrations allowing them to provide detailed insights into asset vulnerabilities and exposure levels. CAASM’s goal is to enable and support proactive risk mitigation and threat response strategies.
4. Continuous Attack Surface Management (CASM)
Continuous Attack Surface Management (CASM) extends the principles of ASM and CAASM by emphasizing continuous monitoring and assessment of the attack surface. CASM solutions leverage automation and real-time threat intelligence to detect changes in the attack surface, prioritize risk areas, and facilitate rapid incident response and remediation efforts. CASM® is also the trademarked name of SynerComm’s flagship platform used to support their Continuous Penetration Testing subscriptions.
5. Penetration Testing as a Service (PTaaS)
Penetration Testing as a Service (PTaaS) is a subscription-based model that provides organizations with on-demand penetration testing capabilities. Penetration testing involves simulating real-world cyber-attacks to evaluate the security posture of systems, networks, and applications. PTaaS offerings allow businesses to conduct regular, but certainly not comprehensive, penetration tests without the need for dedicated in-house resources. PTaaS can support continuous security assessments and the timely remediation of vulnerabilities.
6. Continuous Penetration Testing (CPT)
Continuous Penetration Testing (CPT) involves the regular and automated execution of penetration tests to evaluate the security posture of an organization's infrastructure and applications. Unlike traditional penetration testing, which is conducted periodically, CPT provides continuous insights into evolving security risks and helps organizations proactively address vulnerabilities before they can be exploited by adversaries.
SynerComm's Continuous Penetration Testing Services
SynerComm's Continuous Penetration Testing services integrate elements of CTEM, PTaaS, ASM, and CAASM, with a team of knowledgeable penetration testers, to deliver comprehensive security assessments that are tailored to the evolving needs of modern businesses. Penetration testing can’t (or shouldn’t) be fully automated. SynerComm’s strategy is to automate everything that can be done safely and then rely on experienced penetration testers to do the rest. This includes dozens of monthly and quarterly, pentester performed, “pentest playbooks” plus “emergency playbooks” for new and unexpected threats that emerge. By combining best in class penetration testing with proactive threat exposure management, on-demand penetration testing capabilities, comprehensive attack surface monitoring, and continuous risk assessment, SynerComm enables organizations to stay ahead of emerging threats and safeguard their digital assets effectively.
SynerComm's Continuous Penetration Test approach emphasizes:
SynerComm's Continuous Penetration Testing services combine the benefits of human-led pentesting with their in-house developed CASM platform. Providing modern attack surface management to experienced pentesters allows SynerComm to deliver proactive threat management and continuous risk mitigation capabilities.
[Note: While the definitions provided are based on common industry understanding, specific sources for these terms may vary.]
In the dynamic realm of cybersecurity, the healthcare industry has become a prime target for malicious actors seeking to exploit vulnerabilities and gain unauthorized access to sensitive data. Recognizing the urgent need to fortify the sector against cyber threats, The Centers for Medicare and Medicaid Services (CMS) is leading a groundbreaking initiative. The 2024 cybersecurity rules, unveiled in December 2023 as part of the Department of Health and Human Services' (HHS) broader cybersecurity strategy, aim to establish essential standards for hospitals. This move is poised to enhance the resilience of healthcare organizations against the growing tide of cyber threats.
Recent years have seen a surge in cyber attacks on the healthcare industry, underlining the critical need for robust cybersecurity measures. Cybercriminals frequently target healthcare organizations due to the vast amount of sensitive patient data they handle and their critical uptime requirements. According to recent statistics, the healthcare sector has witnessed a significant increase in the number of data breaches, emphasizing the gravity of the situation.
The 2024 cybersecurity rules proposed by CMS reflect a strategic response to the escalating threats faced by healthcare institutions. The rules aim to set baseline cybersecurity standards that hospitals must adhere to, ensuring a more secure environment for patient data and critical healthcare infrastructure. By outlining specific requirements, CMS intends to raise the overall cybersecurity posture of healthcare organizations, ultimately safeguarding patient information and maintaining the integrity of healthcare services.
While the detailed framework of the rules is yet to be finalized, the emphasis will likely be on crucial areas such as:
The HHS's strategy outlines four key components to fortify cybersecurity in the healthcare sector:
As the healthcare sector faces these challenges, proactive measures based on the HHS's outlined strategy will be instrumental in building cyber resilience, ensuring the protection of patient data, and sustaining the integrity of healthcare services.
Recent reports reveal an alarming surge in cybersecurity incidents within the healthcare industry. In the past year alone, there has been a staggering 50% increase in data breaches targeting healthcare organizations. These breaches expose sensitive patient information, including medical records, billing details, and personally identifiable information.
Ransomware, a particularly menacing form of cyber attack, has wreaked havoc across the healthcare landscape. Statistics indicate that ransomware attacks on healthcare entities have doubled in the last year, with an unprecedented rise in the sophistication and frequency of such incidents. These attacks not only encrypt critical patient data but also bring healthcare operations to a standstill, causing disruptions in services and potentially compromising patient safety.
The impacts of ransomware extend beyond financial losses. Healthcare providers facing ransomware attacks often find themselves in a dilemma, forced to make difficult decisions between paying the ransom to retrieve their data or dealing with prolonged service interruptions. The resultant downtime can lead to delayed patient care, canceled appointments, and an erosion of trust in the healthcare system.
Moreover, the reputational damage inflicted by ransomware attacks can have lasting consequences. Patients, rightfully concerned about the security of their personal information, may seek alternative healthcare providers, impacting the long-term viability of affected organizations.
As the healthcare industry grapples with these alarming statistics, the urgency to implement robust cybersecurity measures, as outlined in the Path Forward on Cybersecurity Improvements by the Department of Health and Human Services (HHS), becomes increasingly apparent.
As the healthcare industry prepares for the implementation of the 2024 cybersecurity rules, the imperative to prioritize cybersecurity has never been clearer. CMS's proactive approach in setting standards reflects a commitment to safeguarding the integrity of healthcare services and protecting patient data. Organizations like SynerComm, Inc. play a pivotal role in helping healthcare providers navigate the complex cybersecurity landscape and meet the upcoming requirements effectively. As we move forward, a collective effort is required to ensure that healthcare remains resilient in the face of evolving cyber threats.
In today's increasingly digital world, the aviation industry is more reliant on technology than ever before. As aviation systems become more connected and dependent on the internet, the risk of cyber threats to airlines and airports has grown significantly. In recognition of this evolving threat landscape, the Transportation Security Administration (TSA) has recently issued a set of new cybersecurity requirements for airports and aircraft. Probably not surprising, the TSA's latest cybersecurity directives emphasize the importance of penetration testing and continuous security monitoring.
The TSA's press release, dated March 7, 2023, outlines the key components of their new cybersecurity requirements for the aviation sector. These requirements aim to bolster the cybersecurity posture of airlines and airports to safeguard critical systems and passenger data. Some of the key highlights include:
Penetration testing, also known as pentesting, is a crucial component of the TSA's new cybersecurity requirements. It involves simulated cyberattacks on an organization's systems to evaluate their security posture and identify vulnerabilities. The importance of penetration testing can be summarized as follows:
In the ever-evolving landscape of cybersecurity threats, continuous security monitoring is vital. This practice involves the constant surveillance of an organization's network and systems to
detect and respond to potential threats in real-time. The significance of continuous security monitoring includes:
The TSA's new cybersecurity requirements for airlines and airports underscore the critical importance of staying ahead of the evolving threat landscape. Penetration testing and continuous attack surface management play pivotal roles in ensuring the safety and security of aviation systems and passengers.
In a world where the aviation industry is more interconnected and dependent on technology than ever before, organizations must embrace these practices to proactively identify vulnerabilities, respond to threats, and safeguard their critical systems. Compliance with these requirements is not just about adhering to regulations; it's about preserving the trust and safety of the flying public. Penetration testing and continuous security monitoring are not just checkboxes on a list; they are the keys to a safer, more secure aviation industry in the digital age.

Having sold and performed assessments and pentests for nearly 20 years, I’ve had plenty of opportunities to hone my strategy and messaging. One common challenge I hear is, “our Board of Directors requires us to rotate vendors” or “our examiner wants us to get a new set of eyes”. This article will explain why I think that could be a big mistake.
Let’s first assume that you’ve done your due diligence and selected a qualified pentest firm with experienced consultants and actionable advice. It’s likely that you’ve tried multiple firms before knowing that you’re working with the firm that best fits your company’s needs. So why change pentest providers once you’ve found the one that’s right for you? Below are my practical responses to these well intended practices.
While there could be worthy arguments for rotating pentesters, rotating pentest firms is risky. If you’ve found a great provider, continue to build that partnership rather than taking risks by starting over with a new firm each year. A good pentest firm can ensure depth and consistency, and they may even help get you out of a jam. By depth, I mean that pentesters thrive and do their best when they collaborate with a team. There’s too much to research, too many blogs, and too many tweets to keep up with everything. When you have a pentester who’s part of a team, you get the combined value of that team. A good pentest firm will also hire and retain sufficient experienced pentesters so you don’t need to worry about the individual pentester on your next engagement.
Consistency is important because a good firm can offer you new pentesters over time while using the same metrics for assessing and reporting risks. The pentesting firm owns the reporting and finding templates, and ensures that all members of the pentest team meet a standard of excellence. Using the same firm for multiple engagements also allows prior notes and findings to be handed off to the next consultant, making subsequent tests more efficient. At SynerComm, we’ve also come to the rescue and helped numerous clients get out of a jam or fill a last second request because of the partnerships we’ve built. It helps to know who you’re going to call when you need help.
This (perhaps poor) advice hinges on the assumption that your current pentester is missing something or will fail to report a vulnerability in the future. If you think that’s the case, then it’s probably time to find a better pentesting partner. The reality is that good pentesters are always researching the latest vulnerabilities and integrating them into their testing methodologies. When a pentester is part of a team that collaborates and shares with each other, the thoroughness and capability of the team grows much faster. If you need a new set of eyes, you really only need a pentest firm with enough qualified and experienced pentesters to offer new resources over time.
That said, I can make strong arguments for using the same pentester several years in a row. Much like an attorney, doctor, or accountant, your pentester should quickly earn a position of high trust. It’s their job to become intimately familiar with your information security strengths and weaknesses. Having the same consultant on a series of engagements is more efficient because they can build on their prior understanding and pick up where they left off. This can provide more depth and more breadth in subsequent projects. It’s common for SynerComm’s clients to request that the same pentester be assigned to multiple engagements, especially with our adversary simulation services (see note at bottom).
Standards and policies are important right up until they start providing bad guidance. For over 20 years, password aging (expiring passwords after a certain amount of time) was considered an important security control. Despite knowing better, even NIST continued to publish security standards stating that passwords should be set to expire after 90 days. For years companies and government agencies required users to frequently change their password and the result was weaker passwords that are easier to guess. My point is that if you’re only switching vendors because you have a policy that says to do so, then this is a good time to reassess that policy. For all the reasons I just described, most companies will make the greatest security improvements by partnering with a great firm staffed with great people.
The next time you find yourself in a position where your policy, board of directors, or examiner tells you to rotate vendors, start a conversation about effective risk management. Finding a great pentesting partner can be a challenge and there is much greater risk in changing firms than sticking with a partner you can trust. A good firm should have sufficient staff and work history to ensure that you can still get a new set of eyes without losing consistency or efficiency. Imagine how much more you can accomplish each year when you’re not interviewing several new vendors, negotiating new contracts, going through legal reviews, and onboarding new vendors. Just like your attorney or accountant, partner with a firm that you can trust to deliver consistent, high-quality engagements over time.
A Note on Adversary Simulations (AdSim): SynerComm uses the term adversary simulation to describe a unique pentesting service we provide to clients. Rather than only presenting and providing a written report, SynerComm’s pentesters offer live demonstrations of common attacks on our client’s networks. Our adsim sessions are 100% collaborative between our client’s defenders and our pentesters. Both sides get to share their screens and ask questions. Our pentesters show how attack tools work and our clients show evidence of their controls generating logs and alerts. When controls are not effective at detecting or preventing attacks, the adsim can be used to retest until they can be tuned or corrected. The adsim also provides invaluable training for defensive teams to see what their controls look like when detecting real attacks.
Our first adsim is always a “pentest replay”, meaning that it’s content is based on lessons learned from a recent external to internal penetration test. The focus is on methods of command and control, privilege escalation, and lateral movement, but always specific to the last pentest. The adsim highlights both attacks that were prevented as well as those that weren’t. Following an initial pentest replay adsim, many clients schedule several additional adsim sessions to further evaluate their controls against specific threats and APTs.
For more information, check out https://www.synercomm.com/cybersecurity/adversary-simulation/

SynerComm's marketing team likes to ask our pentesters for help with their messaging. Like all good hackers, we adapt, automate and improve. So, when we asked our team for some helpful marketing messages, Dylan R. responded within seconds with this.
Password security assessments are important because they help ensure that the passwords being used to protect sensitive information and systems are strong and secure.
Chat GPT - December 2022
In today's digital world, passwords are the primary means of authentication for many online accounts and systems. If a password is weak or easy to guess, it can be vulnerable to attack, allowing unauthorized access to sensitive information or systems. This can have serious consequences, such as data breaches, identity theft, and financial loss.
By conducting a password security assessment, organizations can identify and address any weaknesses in their password policies and practices. This includes identifying and correcting any weak or easily guessable passwords, enforcing password length and complexity requirements, and implementing password expiration and rotation policies.
Overall, password security assessments are a crucial component of an organization's overall security strategy, helping to ensure the confidentiality, integrity, and availability of sensitive information and systems.
Well stated Dylan (or should I say Chat GPT) !!!
A.I. is a powerful tool with endless potential uses. See how SynerComm is using A.I. to enhance our penetration testing and continuous attack surface management (CASM) solutions.

NVIDIA RTX 4090 Unboxing
In February 2017, I co-authored a blog detailing our build of an 8-GPU password cracker. Over the past 8 years, it’s had millions of views and thousands of comments. To all the concerned writers, nothing has melted down and we continue to run 2 nearly identical 8-GPU crackers today. Both are currently running 8 NVIDIA GTX 1080Ti cards.
We also got our hands on one of NVIDIA’s latest cards! We missed the October 12th launch by 9 days but finally found an overclocked Gigabyte GeForce RTX 4090 GAMING OC 24G for sale locally.
Our Goals:
Stay tuned for a future article on our monster RTX 4090 Kracken4 build!!
For our unscientific analysis, we used Hashcat’s NTLM (-m 1000) benchmark (-b) to test our 2 current model cards and the new RTX 4090. This included the NVIDIA GTX 1080Ti, NVIDIA RTX 3090, and NVIDIA RTX 4090.
| Device (as seen by Hashcat) | Hashcat NTLM Benchmark Speed |
|---|---|
| GeForce GTX 1080 Ti, 11039/11178 MB, 28MCU | 66.76 GH/s (28.03ms) |
| NVIDIA GeForce RTX 3090, 23680/24575 MB, 82MCU | 121.2 GH/s (22.55ms) |
| NVIDIA GeForce RTX 4090, 23010/24563 MB, 128MCU | 252.0 GH/s (16.74ms) |
-b and -m 1000 options (-O is applied automatically)When attempting to crack a single NTLM hash using an 8-character brute force crack, the actual average performance was closer to 225 GH/s. Without any tuning and using the latest NVIDIA driver for Windows, the RTX 4090 could brute any 8-character password in approximately 8 hours!
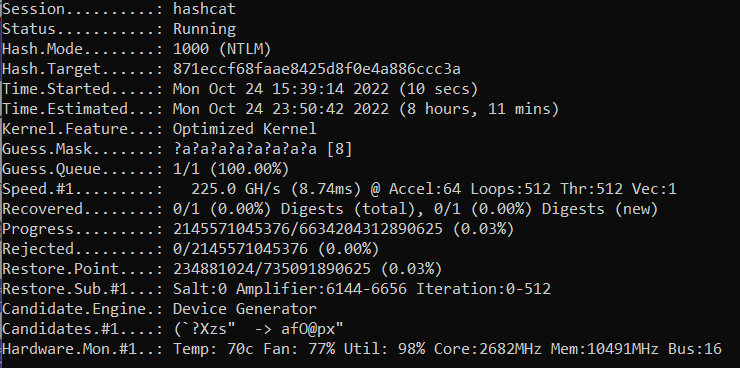
Our early testing shows that the NVIDIA RTX 4090 is a strong contender for high-performance password hash cracking. Despite running the RTX 4090 right out of the box without any tuning on a Windows 11 desktop computer, the cracking performance is amazing. When compared to our current cracking rigs with 8 GTX 1080Ti cards, a single RTX 4090 is roughly 48% as powerful. That makes the RTX 4090 almost 4x faster than the GTX 1080Ti. Stay tuned as we figure out how many 4090’s we can get our hands on and combine into a single cracking rig.
Interested in learning more about SynerComm's password cracking services? Check out this page!
I can remember it like it was yesterday... Casey, Hans, Jason, Scott, Sam, Bill and I were slowly destroying my hotel suite at Circle City Con while trying to win the 2015 CTF. (We took 2nd place and never got our GoPro prize... still sour, can you tell?) Amongst all the teams’ brilliant ideas that evening, was that we really needed a blog. A few hours later, #_shellntel was born.
Our intent was (and still is) to focus on pentesting, hacking and offensive security; we feared that some articles may be too edgy for some corporate/professional readers. Therefore, we separated our #_shellntel articles from other SynerComm blogs. Over the past 7 years, things have changed and today everyone loves pentester articles.
We are grateful for the loyal support of our #_shellntel readers throughout the years. Please continue to read about the latest IT news, tech trends, and cybersecurity threats on our new blog at www.synercomm.com/blog or link directly to our #_shellntel articles at www.synercomm.com/blog/tag/shellntel/. All of our existing content was moved, and all new articles will be published here going forward.
Thank you always,
Brian Judd, VP Information Assurance
SynerComm, Inc.
Warning: This blog contains purposeful marketing and gratuitous plugs for SynerComm’s CASM™ Subscription services. Seriously though, the following article will present the need for better external visibility and vulnerability management.
Whether you are vulnerability scanning to meet compliance requirements or doing it as part of good security practices, there is a universal need. At the time of this article, there are essentially three equally capable and qualified scanning solutions. They include products from Tenable, Rapid7 and Qualys. My point is that each of these scanning solutions, if configured correctly, should produce accurate and similar results. Therefore, as long as your scanning provider is using one of these three solutions, they should be able to detect vulnerabilities. SynerComm starts with a top scanner and then addresses all the gaps that your MSSP is missing.
Vulnerability scanning and analysis is a critical process within all information security programs. Scanners should find missing patches, dangerous configurations, default passwords, and hundreds of other weaknesses. Their technology is based on probing systems over networks and trying to determine if the system exhibits specific vulnerabilities. While the process itself isn’t complicated, many organizations choose to outsource it to a managed service provider. If you need a provider or already have one, it’s time to upgrade to Continuous Attack Surface Management (CASM™).
Vulnerability scanning MSSPs served their role well for many years but failed to keep up. They failed to keep with cloud migrations, failed to keep up with the rate of IT changes, and failed to provide tools that simplify and enable security for their subscribers.
If you’ve ever wondered what your systems and exposures look like to a cyber-criminal, just ask a pentester. SynerComm’s CASM® Engine was originally designed to provide accurate and timely reconnaissance information to our penetration testers. Access to this data and our ‘Findings-Based Reporting’ is available to all CASM® and Continuous Penetration Test subscribers.
Learn more about our Continuous Attack Surface Management and our industry-leading Continuous Penetration Test subscriptions.
| VS-MSSPs | SynerComm CASM® | |
|---|---|---|
| Scheduled Scanning of Known Assets | ✔️ | ✔️ |
| Ad-Hoc (Manual) Scanning | ✔️ | ✔️ |
| 24/7 Online Dashboard Reporting | ✔️ | ✔️ |
| Discovery of New Assets | ✔️ | |
| Elimination of False-Positives | ✔️ | |
| Validated Findings | ✔️ | |
| Risk-Based Customizable Alerts | ✔️ | |
| Access to Penetration Testers | ✔️ |
Coming from someone who can officially say that information security has given me a few gray hairs, I'm writing this article from the perspective of someone who's been around the block. With over 15 years in information security, I feel like I've seen it all. And while I can't claim to be a great penetration tester myself, I can say that I work with (and have worked with) some truly talented pentesters. I can also feel confident stating that I've read more pentest reports than most.
So, having this background… I get asked by businesses and defenders all the time, "What advice would you give?" and, "What lessons can be learned?"
Well, thanks for asking…. (insert deep breath here)
In fact, we've known that passwords are a weak form of authentication since the moment the first password-based authentication system was created. Passwords can be weak for several compounding reasons. Whether it be due to their limited length and complexity (keyspace) or the fact that they can be shared, guessed, written down, or reused, let's face it, they provide almost no security. Until we stop using passwords or ensure that every last account has a strong and unique password that can't be guessed or cracked, we accept significant risk.
(MFA) is not enabled or required for all remote access. While it is almost common place now to find MFA on VPNs, we still find roles, groups, and even URLs allowing MFA to be bypassed. Further, other types of remote access like Citrix and Remote Desktop, Outlook Web Access, and SSH are more overlooked. Remember that when passwords are weak (and they probably are), attackers will be quick to take advantage when MFA is not enforced.
Your mom said it, and now I will too. In SynerComm's reporting, we consider both #1 and #2 to be high-severity findings in our pentest reports. When combined, these result in a critical weakness. Password spraying allows an attacker to easily guess common passwords (think Summer19) and gain immediate access to email and internal networks.
Don't get me wrong, get your EternalBlue and Heartbleed patched, but don't think just because you're well patched that you are secure. Vulnerability scanning is important, but at its best, it discovers live systems, missing patches, default credentials, weak services, and other well-known vulnerabilities. What it doesn't tell you is that your systems may already include a roadmap to access anything and everything on your network.
Pentesters, just like modern attackers, typically don't rely on missing patches to traverse networks, gather privileges, and access protected data. No vulnerability scanner will warn you that all laptops share the same local administrator password or that a domain admin RDP'd into one of them to troubleshoot an issue (and left their cleartext password cached in memory).
Again, don't get me wrong, I am a big fan of solutions like Palo Alto and CrowdStrike. BUT, simply purchasing and deploying these solutions doesn't make your networks and systems more secure. Like any control, all security solutions must be configured, tuned, and VALIDATED.
Lesson #5: It isn't uncommon to find best of breed security controls running in "monitor only" or "log only" state. After all, the easiest way to start is to convert that old layer 3 ASA config and turn on the security features later. And let's not forget that ALL IT EMPLOYEES should always be whitelisted in these controls because we don't need that stuff in our way.
Contractual, industry, and especially regulatory compliance are all important, but don't let compliance get in the way of being secure. Information security programs should be designed to protect the confidentiality, integrity, availability, and usefulness of information; compliance should just be a benefit of good security.
Secure coding isn't a new concept, but the concept is (unfortunately) new still to many developers. Widely-used and commercial off the shelf (COTS) applications are heavily scrutinized, but your applications may be waiting for the right attacker to come along. A lesson worth sharing is that a breach can be far more costly than validating and potentially fixing issues before the attack.
If you've made it to this point, thank you for reading through. This often isn't what people expect to hear or even want to hear, but sometimes honesty can be blunt and surprising. My advice is always start with a solid foundation and then build on it. Use frameworks like the CIS Top 20 to provide a prioritized roadmap and don't get caught skipping ahead. Good security can be as simple as keeping to the basics.