The shellntel team attended Circle City Con this year and participated in their second annual Capture The Flag tournament. While there was many great things at the conference, this event held our attention for its majority as we spent the majority of our time solving the puzzles. In the end, we ended up taking second place over all. Contained below is our write up of the challenges we solved. Congratulations to the winning team: (TEAM XSS). We look forward to trying this again next year.
This challenge was all about locks. Apparently the trick to learn with these was utilizing top torsion. To my knowledge, no other team got the 100 point lock.
This was solved simply with strings:
(~/CTF/CCC2015/OpenSesame:kali)> strings pwchal1 /lib64/ld-linux-x86-64.so.2 CyIk libstdc++.so.6 __gmon_start__ _Jv_RegisterClasses ... REMOVED ... CXXABI_1.3 GLIBCXX_3.4 []A\A]A^A_ SetecAstronomy Ah ah ah, you didn't say the magic word! Enter the password: A winner is you! ;*3$" zPLR
Clearly the answer here was "SetecAstronmy"
We use strings here again, but notice that the answer looks to be a hash or encoding of some time. Base64 was found to be the right encoding.
(~/CTF/CCC2015/OpenSesame:kali)> strings pwchal2 /lib64/ld-linux-x86-64.so.2 CyIk libstdc++.so.6 __gmon_start__ ... removed ... GLIBCXX_3.4 <=t- []A\A]A^A_ Ah ah ah, you didn't say the magic word! Enter the password: A winner is you! V2VBcmVBbGxSdXRoTWFyeA== ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/ ;*3$" zPLR (~/CTF/CCC2015/OpenSesame:kali)> echo "V2VBcmVBbGxSdXRoTWFyeA==" | base64 --decode WeAreAllRuthMarx
Answer: "WeAreAllRuthMarx"
Strings to grab the key. We tried decoding this with base64, but the result seamed garbled. Turns out we had to decode it twice.
(~/CTF/CCC2015/OpenSesame:kali)> strings pwchal3 /lib64/ld-linux-x86-64.so.2 CyIk ...snip... GLIBCXX_3.4 <=t- []A\A]A^A_ Ah ah ah, you didn't say the magic word! Enter the password: A winner is you! UTI5eWNHOXlZWFJsUVdOamIzVnVkSE5RWVhsaFlteGxUbWx1WVZOd1pXRnJhVzVu ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/ ;*3$" zPLR
(~/CTF/CCC2015/OpenSesame:kali)> echo UTI5eWNHOXlZWFJsUVdOamIzVnVkSE5RWVhsaFlteGxUbWx1WVZOd1pXRnJhVzVu | base64 -d | base64 -d CorporateAccountsPayableNinaSpeaking
Strings to get the key, but the result was not base64 encoded (no matter how many times we tried decoding it. Someone pointed out the string length looked similar to that of the md5 hash, and the title of the challenge "maryland five easy" or MD5 certainly pointed us in the right direction. Loading the hash onto www.hashkiller.co.uk resulted in our answer:
(~/CTF/CCC2015/OpenSesame:kali)> strings pwchal4 /lib64/ld-linux-x86-64.so.2 CyIk libstdc++.so.6 __gmon_start__ []A\A]A^A_ %02x Ah ah ah, you didn't say the magic word! Enter the password: A winner is you! c61bf5c113765a4e721acbfc43116be8 ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/ ;*3$" zPLR
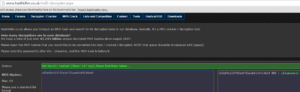
Same as the others, used strings to get the key, and with the clue of "Mary Land Hard" we know this was also going to be a md5 key.
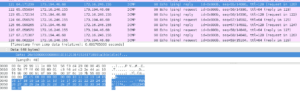
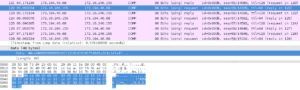
This was a pcap file containing mostly pings. Our only clue was "There's a glitch in the matrix... when did it happen"? First thing we did was split the pcap into protocols, first checking the arp packets, they looked fine. Then the UDP packets, some of these packets were related to DropBox's Discovery Protocol. I wasn't too familiar with this and figured I'd come back to it later if ICMP didnt yield any useful results. Checking ICMP revealed 151 requests, and 150 replies. Our first thought was the time stamp of the last sent packet where there was no reply. This was not correct, so we then looked at the packet contents of each ping and noticed that packet 122 within the stream had a different payload than the others. The correct answer was the timestamp of the packet 122: 65.055634 (note: we initially failed by changing the displayed time stamp in wireshark from relative time to UTC standard, so while we had the right answer, we had the wrong format. Frustrating)
The title of this challenge was "The fabric of reality" and since there was a large quilt hanging in the CTF room we assumed correctly that this was related to the quilt.

At first glance this appeared to be a frequency related challenge, so we performed a frequency analysis and substituted characters according to their frequency in the English language (https://en.wikipedia.org/wiki/Frequency_analysis). After using that method for a while and not making much progress we went back to inspect the quilt and found that the challenge had been created by Mike Connor. Upon searching for Mike we found that he did a similar challenge for PauldotCom's episode 350.
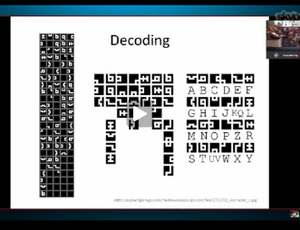
Using this new knowledge we were able to produce a this:
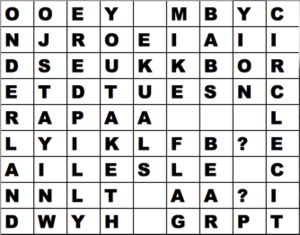
And ultimately solve the challenge with: youtaketheredpillyouleavewonderland
This challenge consisted of a wave file called output.wav. When played we heard a series of highpitched noises. Slowing them down it sounded as if they were Morse Code. We initially tried solving it by hand, but figured there's probably a phone app for this, and sure enough there was. The code appeared to repeat the same thing over again, which was a URL shortened link: HTTPS//GOO.GL/W0WUOS which lead us to https://twitter.com/revrance/status/600037250496212992. Since the answer was two words we tried: "almost famous..." which was correct (periods included)
This challenge stated that "Frank the Fixer" was dropping code. Searching github for his twitter handle "TheDevilsVoice" we were able to find a file called "iknowkungfu". While inspecting this file we found that it was double-zipped. Upon decompression we found that the contents were URL encoded. When decoded this lead to a link (http://imgur.com/ndrSPRx).

Scanning the qr code lead to this image and the flag:
For this challenge we needed to identify the local of the person in the picture. The picture had an iconic building in the background. Using the John Hancock building as our point of reference we navigated using google earth to the location we believed he was staying and submitted the simple street address as our answer, which was correct.
We were given the simple string "UnpxGurCynarg!!!!bar!!11ryrira1!" which appeared to be ROT13 encoded to be: "HackThePlanet!!!!one!!11eleven1!"
The team had a blast. A huge thanks the CircleCityCon staff who put this together!

The 2015 CTF shellntel Team